Recent reports have indicated that the actors behind Dridex, originally a banking Trojan distributor, have switched tactics, and are now heavily pushing out a new ransomware called Locky.
The current method of distribution is via a spam email, which contains a Word document. Additional reports have stated that it is being distributed via the Neutrino Exploit Kit.

Note, the file name may be different for every email sent, but the file will always be a Word document.
If you open the email, you’ll see an alert by Word, which warns you that the document contains a macro. Macros allow users to “code” specific procedures into the document, to help automate or repeat specific tasks.
However, in the case of Locky, it is used to install the malware on the machine.
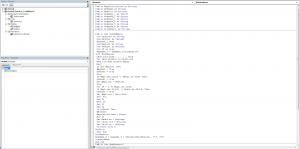
This is a screenshot of the actual macro that delivers Locky.
If you happen to ignore the alert from Word, and clicked on Enable content, Locky will scan your system for specific files, and will encrypt them, or modify them so that you cannot use them anymore, unless you pay the ransom.
The files it encrypts are commonly found on end users’ machines, such as .doc, .csv, .pdf, .jpg, etc. However, what should be more concerning to enterprise customers is that it will also look for .SQL, .SQLiteDB, and .SQLite3 files, which are associated with databases. Additionally, it looks to encrypt encryption keys (.crt and .key).
Once the malware has been executed, the Desktop wallpaper may change, to show instructions on how to decrypt your files.
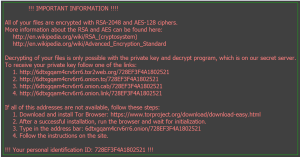
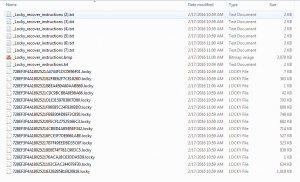
It will also drop text files that contain the same instructions on how to decrypt your files. These files are named _Locky_recover_instructions.txt.
The transaction is all too familiar for many of the other types of ransomware out there. The malware authors have you visit a website, hosted on the TOR network, to provide payment. For Locky, the current amount is .5 BTC, or the equivalent of $209.33.
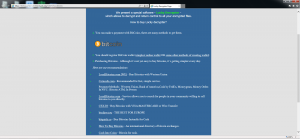
Bitcoin site hxxps://6dtxgqam4crv6rr6.tor2web.org/728EF3F4A1802521
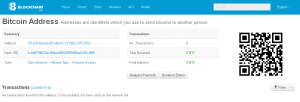
We’ve looked into the Bitcoin address, 151xDKSeevSsBYu4oeFczYSb5z7UPY35zv, but currently do not see any transactions.
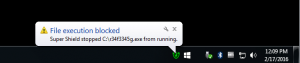
PC Matic users should know that this malware is blocked, and cannot be executed on machines protected with Super Shield.
You can read additional information about Locky Ransomware here.