




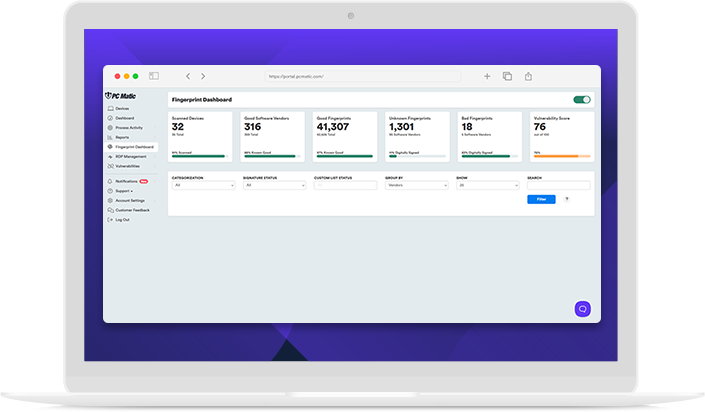
Enhance your customer onboarding with a streamlined dashboard that easily supports even the most customized applications. Gain full visibility into your environment by reviewing each device's security profile, complete with meta-data and device history. Simplify your security management by applying allowlist or blocklist restrictions across devices with a single click. With our system, you can score each device's vulnerability, giving you clear insights into your overall security posture. And with PC Matic's malware intelligence, you can confidently categorize and protect every device in your network.
Named to the National Institute of Standards and Technology (NIST) National Cybersecurity Center of Excellence
Delivers application allowlisting as well as certificate and script allowlisting to defend against fileless attacks
Our industry leading platform empowers your team with intuitive tools and capabilities to manage this vital layer of protection efficiently
A product that can be layered into your current endpoint security stack alongside an existing security solution
A scalable prevention layer with US-based support operating on an extended hours schedule
Deploy across thousands of endpoints in a matter of hours
Tier based pricing and dynamic lead sharing helps you drive profits for your business without having to sacrifice the time you spend on finding new customers and keeping your existing ones.
Increase your efficiency with cloud-based management and built-in remote monitoring, and stop reacting to malware with PC Matic's prevention first security.
Dedicated onboarding, continued support teams, NFR internal licenses and flexible monthly billing means you can focus on what really matters; keeping your customers secure.

Small businesses across the world need your help to defend against cyber attacks. With PC Matic MSP, you apply a proactive and preventative approach to security for your own network and your customers. PC Matic MSP uses allowlist technology to prevent unknown malware and ransomware, advanced heuristics to block script-based attacks and keeps unauthorized devices from utilizing Remote Desktop Protocol in your network.