A few days ago, Kayla wrote about Fileless Malware, and how PC Matic protects your devices from it. Malware can be so complicated and confusing to understand, that Malware Research is a full-time job… Let alone “fileless” malware. However, when explained in the proper steps, the concept is actually very easy to understand and every PC user should know the basics in order to keep him or herself up-to-date on the latest security concerns. In order to understand fileless malware, let’s first quickly go over how “standard” file-based malware works.
Regular (File-based) Malware
Step 1 – The victim unknowingly clicks or is tricked into clicking on a link, email attachment, or even a file off of a USB drive or other file storage
Regular, file-based malware generally does not require a ton of effort to execute, but it still does require the user to download or otherwise run an executable file. For this reason, clever and deceptive emails are often used to distribute it, as well as deceptive file names, and even spoofed certificates which impersonate a legitimate company. Another avenue of delivery for file-based malware is via USB storage, CD, DVD, Blu-Ray, etc… Once the file is opened up, the malware takes over from there.
Step 2 – Execution
The file-based malware executes and takes control over the machine. Sometimes it will write new files to the drive, place entries into the Windows Registry, inject malicious code into legitimate processes that users know and trust to avoid detection, record keystrokes, give an attacker command over the machine, and a whole lot more.
How Standard Antivirus works
The most powerful way that most antivirus software works is that, upon download and/or execution of a potentially malicious file, the antivirus scans this file for known signs of – or “signatures” – of a bad file. These signatures can be hard-coded evidence of a specific threat, but they can also be patterns which add up to a suspicious file. You may have heard the term “virus definitions” in the past, which are descriptors of such bad files, often called “blacklisting.”
As you may know, PC Matic SuperShield offers superior protection from the cyber world’s worst threats because it, unlike other antivirus and antimalware solutions, automatically blocks all bad files by default without the need for signatures or definitions first. It does this by using process hooking technology, which intercepts every single process before it is run on the machine.
Fileless malware has no files or has none upon initial infection. This means that there is no way for a traditional antimalware solution to scan a file as it’s downloaded or when it is executed. So what’s the big secret?
How Fileless Malware Works

Fileless malware takes a completely different approach to infecting a machine. Instead of getting the user to download a bad file and run it, it instead uses legitimate programs and tools already on the machine to do bad things. This is a very important point because that means that there are no “suspicious” programs running in memory. The programs that will be carrying out the malicious attack are actually legitimate, trusted Microsoft programs. How is this possible? To understand, we need to quickly go over scripting. If you are already familiar with what scripting is such as Python, VBScript, Powershell, JavaScript, Ruby, etc… Then you may be able to skip the following section.
What is scripting and how does it relate to fileless malware?
There are several tools that a programmer can use in order to get a computer to follow instructions. Two popular ways are compiled-language programming and interpreted-language programming, also called “scripting.”
While this may sound confusing at first, the concept is actually very simple: Compiled-language programming generally takes a programmer’s written code and translates it directly or indirectly into machine-code which is read and understood by the computer processor inside of the machine the user is running. This is also sometimes referred to as “native code” because the end-result file is written in the processor’s “native tongue.” The compiler itself is actually just another program which takes a programmer’s code in and spits out the machine code. This means that .exe files and .dll files often contain processor instruction codes specific to the processor model for which the program was intended to run on, which is why when you try to open one in notepad it looks like gibberish. So malware that has been programmed in compiled languages like C, C++, Delphi create these executable files which have plagued computers for many years and often are what virus definitions are looking for.
In contrast, an interpreted scripting language, such as Python, JavaScript, and Ruby does not get compiled to machine code. A program written in a scripting language is called a “script” and it remains as a text file forever. In fact, scripts themselves are simply plain text and you can see for yourself by right clicking on one and opening it in Notepad, for example… Unlike the .exe or .dll files, the text is human-readable.
What this means is that a script is simply a text file of source-code; to the computer processor, it makes no sense, and in fact, it cannot be executed directly. To run a script, the client machine must have the language “installed” which simply means that in the background on the computer, there must be a program called an interpreter (also called an “engine”) installed. This interpreter is a compiled program and is able to directly control the processor even though the script itself cannot. The interpreter reads the plaintext script file as input and then controls the machine. A final point is that interpreters can directly execute instructions passed to them without them being in a file at all. For example, if you have Python installed on your computer, you can simply open up the “Python Shell” and type Python code into it, executing it in real-time. There is no need for a Python file unless you want to store your code for future usage.
Let’s now talk about why this is so significant. This means that instead of placing a bad executable file on a machine to take control of it, text instructions can be sent to the machine and then executed by a trusted program that is already on the machine. Let’s look at the following example:
Bob is a bad guy, and he wants to destroy Alice’s computer. Alice has Python installed on her computer because some programs that she needs to use for class require it.
Bob emails Alice a malicious Python script, and by opening up the script, the Python interpreter destroys the machine under the direction of the script.
No antivirus would have detected this because the script file that Bob sent Alice is not considered an executable program.
However, this is still not fileless malware. We’re going to tweak a couple things and it’ll all make sense.
In the Real World
In reality, Python was a great example of a scripting language and is very well known, but in fact it is not needed at all in order to carry out one of these attacks. It turns out, all Microsoft Windows installations ship with a powerful command-line utility and scripting language called PowerShell. Many businesses and IT professionals use PowerShell to automate tasks much like Python, however, PowerShell is more powerful on a Windows machine and it is exclusive to Windows machines.
It also turns out that web browsers, such as Chrome, Firefox, Internet Explorer, and Safari, are also script interpreters. You may have heard of the language called JavaScript. Much like Python and PowerShell, JavaScript also has an engine which is actually a compiled, native program, often written in C or C++ which reads the textual scripting language and then controls the computer based off of what the script tells it to have the computer do.
There are ways for JavaScript (or JScript, an implementation of JavaScript on Windows) and/or Visual Basic Script (VBScript for short) to be embedded into an HTML webpage, such as the one you are currently looking at. In addition, your PC comes standard with several programs already installed which are capable of executing scripts like Windows Script Host (WScript.exe and cscript.exe), PowerShell, and Microsoft HTML Application (mshta.exe).
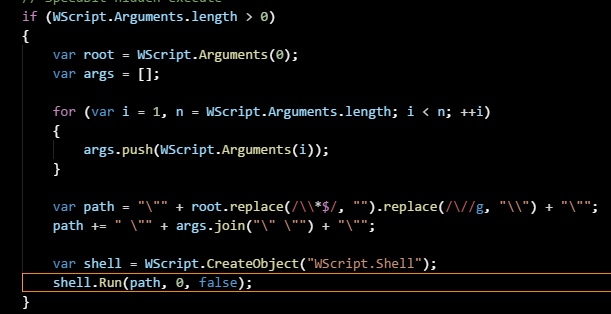
The malicious scripts could be in a text file, or they could simply be embedded in a website and they have the ability to open up a command prompt such as PowerShell, cmd, or another, or run another script interpreter like WScript, a web browser, or an HTA without the user even clicking anything at all. Inside of this command prompt, malicious code can be executed and/or passed off to WScript. Malicious script can simply be executed on the fly, by the interpreter without ever having to be saved onto the disk at all. Below is one such example of code. As you will see, it is actually quite simple:
The Windows Registry
The last topic we need to cover is persistence – how does fileless malware actually reside on the machine after its initial launch? There are several ways, but one way in particular is especially clever. Of course the script could actually write files to the disk, essentially become a file-based malware. Or… Where else is a suitable place designed specifically to store text on a Windows system? The Registry! Since plain text and an interpreter is all that is needed in order for a script to run, Windows comes with an interpreter, and the Registry is a file-less way to store plaintext, we have the perfect combination for malware authors. The Windows operating system provides ways to run legitimate system executables on bootup or some other specified time, such as services, scheduled tasks, and specific registry entries which are evaluated when Windows starts. At first, this would appear harmless, but these “legitimate executables” can actually be interpreters such as WScript and MSHTA mentioned above. So the malware can place a registry key with an instruction like this:
wscript.exe //B C:\Users\You\AppData\Local\some_malicious_script_text_file.txt
The //B argument passed to wscript.exe also silences the program so that if there is an error, it will silently quit so as to not alert the user.
This script could also launch other scripts. Alternatively, the registry entry could launch PowerShell and PowerShell has the capability to directly execute extremely powerful operating system functions to perform other attacks and essentially take over the machine. PowerShell also allows for direct execution of C#/.NET code, also very powerful, in a similar manner that Python can be entered into the Python Shell to execute scripts.
Conclusion
Scripting attacks pose an extreme and unique security risk and require a different protection model than standard file-based threats. PC Matic is currently the only anti-malware solution which offers exclusive protection against these scripting attacks, in addition to standard file-based attacks. There are other ways to prevent such attacks, such as attempting to disable as much scripting support as possible in addition to running your web browser in a sandboxing program. However, these other options can be incomplete (for example, disabling scripting in Firefox or Chrome, but WScript can still be run anyway) or cumbersome and unrealistic. Sandboxing is indeed very helpful, but it can pose challenges and get in the way when a user needs to download many files straight to disk or have direct access to their file system. This is Why PC Matic is a great choice for protecting yourself from these attacks while also sparing you of the hassle of sandboxing and/or incomplete protection.
The key point to take away from this article is the difference between a fileless/script attack and traditional file-based malware is that instead of sending a malicious program file to a victim, the attacker sends malicious instructions to an otherwise legitimate program, and then that program in turn executes the bad malware instructions. Due to this fact, file-based scanning will not stop these attacks since the programs which perform them are trusted scripting engines like your web browser, WScript, PowerShell, etc… rather than malicious files.
Hopefully this clears up any confusion on fileless malware. Feel free to drop any questions in the comments! Til’ next time.