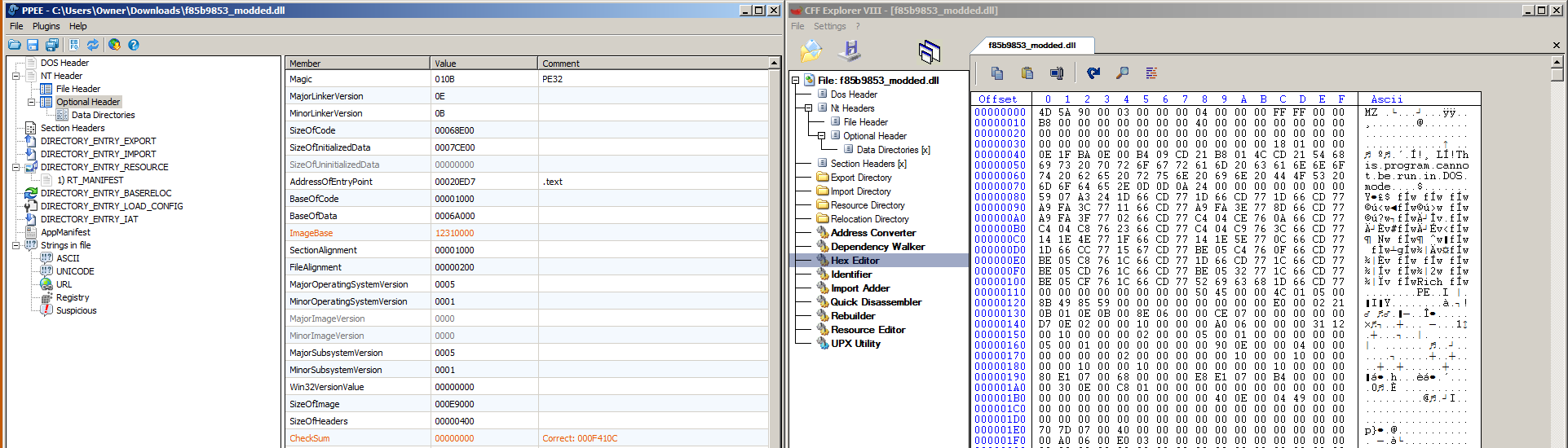
Worms, Trojans , and Rootkits are not the same.



Today I wanted to take the time out to inform or educate you on the names and differences of not so good files that you may come into contact with. Thus, making having a superb antivirus software like PC Matic and Super shield a necessity. A lot of times the word virus, worm, Trojan, and Rootkit are used interchangeably when in fact they mean different things and have different ways they can wreak havoc and compromise your system.
First, I would like to start with what a virus is and what it does. A virus is a program that reproduces itself into other programs and files usually with malicious intent. You may be asking yourself, how do I know if I’ve been infected with a virus? The symptoms of a computer being infected with a virus are as follows: high CPU utilization, lost hard drive space, corrupted data, private information compromised, and pop-ups to name a few.
Next, we will talk about what a computer worm is and the effects it has on your computer. A worm is something that clones itself without the use of another file or program, unlike a virus. They utilize networks and depend on security vulnerabilities to infect other computers. It does not alter files but lives in active memory and recreates itself. As a result, you would experience high CPU usage and slowness of the worst kind.
Our next specimen for discussion is a Trojan Horse or just Trojan for short. A Trojan is a sneaky piece of malware and a hacker’s best friend. They are mostly distributed through social engineering attacks. They are different from viruses because they don’t have the ability to replicate themselves but just as dangerous and can have catastrophic effects on your system. Once a computer is infected with a Trojan it can assist an attacker with stealing confidential information like passwords and credit card information even turning on your webcam without your knowledge or consent.
And lastly, we will discuss what a Rootkit is. It is a type of Trojan that seeks to gain root or administrative access. It has the ability to conceal itself, other files, registry keys, and network connection and keep them hidden from being discovered. Removal of this type of infection can prove difficult or impossible and in some cases reinstalling the Operating System is the only way to clear the infection.
There are many threats and dangers when it comes to surfing the internet, downloading files, and clicking on links. That is why it is crucial to have an antivirus software active and running at all times. I have blocked many Ransomware Viruses and Trojans during my shift as a malware researcher and stand behind Super Shield as being the best real-time protection that you can get on the market today.
I hope this blog helps. Cheers.