Hackers work through the holiday to send out text message phishing attacks to American Express users…
Shortly after dinner on Labor Day evening, I received a text message from “417-82” indicating that I should review my American Express profile.
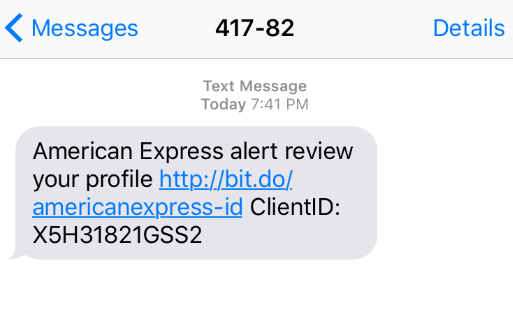
The text message had a link, which utilized a URL Shortening Service, to make the URL smaller, so it fits on text messages properly.
Being the security conscious person that I am, I immediately logged into www.americanexpress.com, and checked to make sure everything was OK. It was.
Next, I wanted to see where the URL in the text message was redirecting me to. I opened up a browser on my virtual machine, and found that the URL, hxxp://bit.do/americanexpress-id, redirected me to hxxp://mcexclusiveclub.com/LogonHandler. Once I put in a fake username and password, I was redirected to hxxp://segurainformatica.com.br/myca/logon/us/action/LogonHandlerAcc/details.htm
Let’s try to piece together the phishing attack.
We know by visiting mcexclusiveclub.com, that the WordPress site was clearly compromised by a hacker. The reason we know this, is that when you visit the site, you see an open directory of files. In addition to the benign files, the site also contains the phishing page, plus a file called shell.php, which is detected by several antivirus companies as malicious.

Compromised website, showing shell.php
Once the hacker got “shell” access, or direct access to the webserver, he began uploading a website that mimicked the real American Express site. They used the initial site to load the login page, then redirect to another URL, where additional personally identifiable information would be requested.
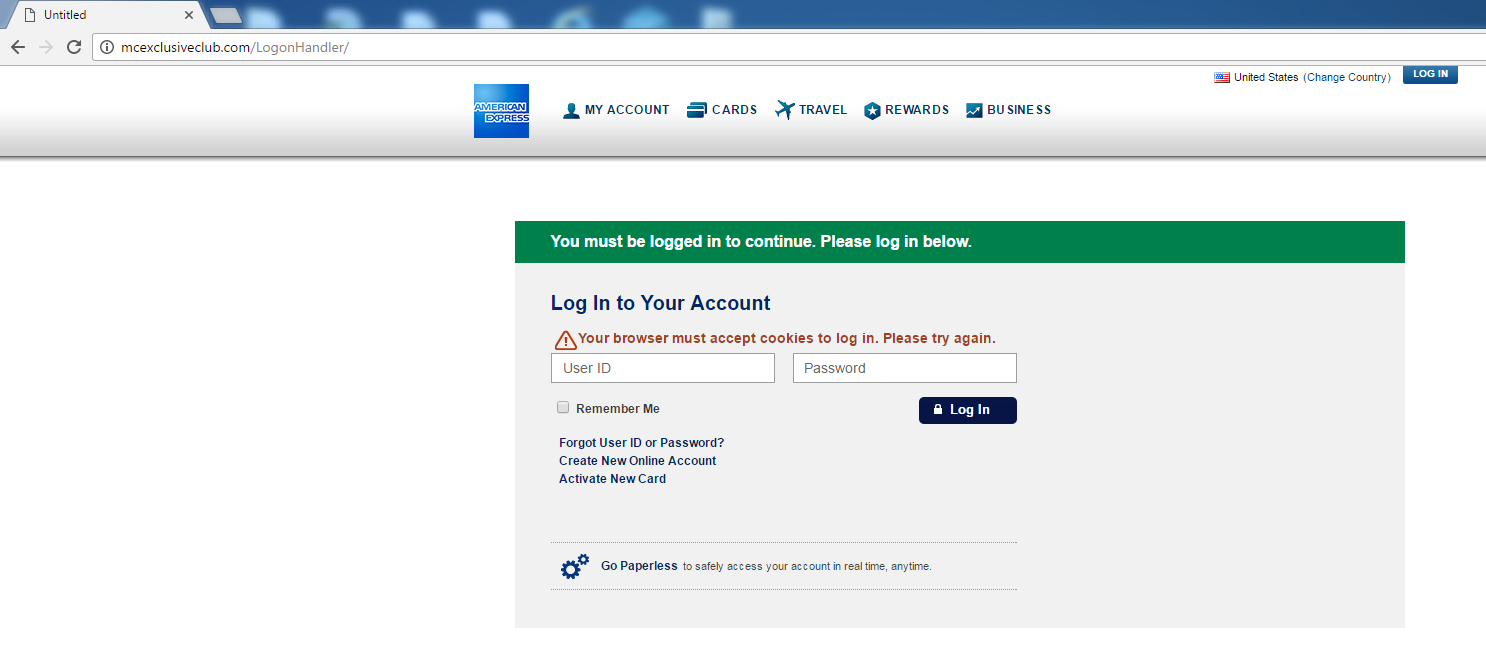
A screenshot of the initial phishing site
The site hxxp://segurainformatica.com.br happens to be running Joomla, a content management system, or CMS. More than likely, the owner of the domain has not updated Joomla and the plugins that it is running, leaving it vulnerable to attacks.

A screenshot of the redirected phishing site
If you were to fill in the information on the phishing page, the hacker would receive an email with your username and password, and all of the account information you entered in the form.
In efforts to reduce the number of people becoming victims of this phishing attack, I pulled up the “Whois” report on the domains, to see if there were any abuse email addresses I could contact. Thankfully, there were abuse email addresses listed, so I have reported the sites, so that they are taken down.
Hackers are getting crafty, and we all have to be on alert for these types of attacks. Emails aren’t the only way hackers are trying to get your personal information and credit card numbers. In addition to these text messages, hackers are also pretending to call from actual corporate phone numbers, impersonating the real credit card company. If they do call you, immediately hang up. Call the number that is listed on the back of your credit card, to verify the issue. If you get a text message, don’t click on the link. Simply go directly to the credit card company’s website, or pick up the phone and call them.
Stay safe!




