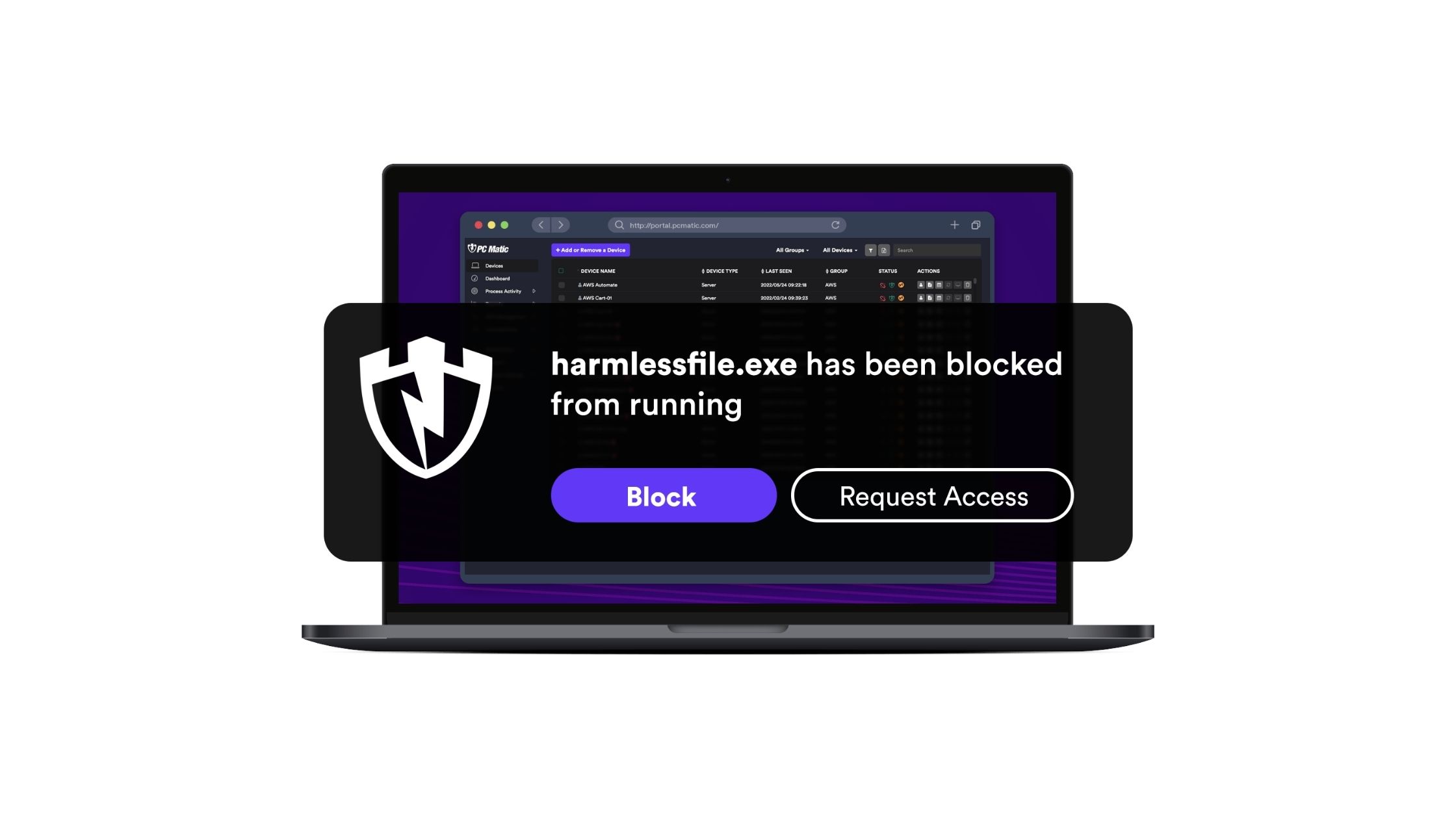
How PC Matic’s Application Allowlisting Protects Operational Technology
Cyberattacks pose a growing threat across industries, but operational technology (OT) environments face unique security challenges. Unlike IT networks, which benefit from traditional antivirus solutions, OT systems often operate on legacy infrastructure, prioritize uptime, and have limited connectivity. As a result, standard cybersecurity tools fall short in protecting these critical systems. At PC Matic, we […]
How PC Matic’s Application Allowlisting Protects Operational Technology Read More »