In the fast-paced world of technology, even minor glitches can send ripples of disruption across the globe. Such was the case with the recent CrowdStrike outage, which unfolded due to a faulty software update. This incident didn’t just inconvenience millions of Crowdstrike customers; it highlighted significant vulnerabilities and gave cybercriminals a golden opportunity to exploit the chaos through phishing scams. In this blog, we’ll delve into the details of the CrowdStrike glitch, its immediate consequences, and the ensuing wave of phishing attacks, offering practical advice on how to stay safe in the aftermath.
The CrowdStrike Glitch: A Global Tech Hiccup
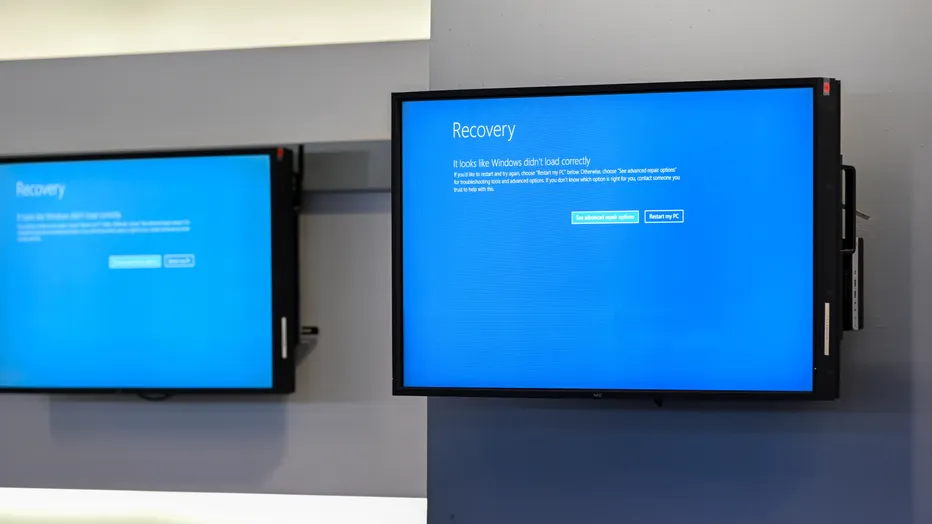
On a seemingly routine Friday, a CrowdStrike update designed to enhance cybersecurity ironically caused widespread disruption. The faulty update caused blue screens of death on Microsoft Windows machines, disrupting millions of Windows computers worldwide, triggering system crashes, and leaving users scrambling to restore normalcy. Businesses across various sectors, including airlines and emergency services, grappled with significant operational challenges.
The incident underscored the modern world’s dependence on cybersecurity software. When a company like CrowdStrike, renowned for its cutting-edge security solutions, experiences a malfunction, the ripple effects can be profound. CrowdStrike moved quickly to identify and resolve the issue, but the damage had been done, leaving a lingering sense of vulnerability.
Phishing in the Aftermath: CrowdStrike Emails You Can’t Trust
Threat actors are always looking for opportunities to exploit confusion and uncertainty, and the CrowdStrike outage provided just that. In the days following the incident, security researchers reported a surge in phishing emails masquerading as official CrowdStrike support communications. These fraudulent emails aimed to trick recipients into clicking malicious links or divulging sensitive information.
Tactics Employed by Cybercriminals
1. Urgency:
Phishing emails often create a sense of urgency, claiming to offer critical fixes related to the recent outage. This tactic targets the recipient’s fear of further disruptions.
2. Fake Authority:
These emails frequently use official-looking logos and language to appear legitimate. This veneer of authenticity can easily deceive even the cautious user.
3. Threats:
Some emails may threaten account suspension or heightened security risks if the recipient doesn’t comply with the instructions, compelling quick, unthinking action.
Staying Phish-Free: How to Spot the Fakes
Awareness and vigilance are crucial in combating phishing attempts. Here are some practical tips to identify and avoid falling victim to these deceptive emails:
Check the Sender:
Always verify the sender’s email address. Official communications from CrowdStrike will come from a legitimate domain (e.g., @crowdstrike.com).
Beware of Urgency:
Legitimate companies seldom pressure you into immediate action. Be wary of emails that demand quick responses or use scare tactics.
Don’t Click on Links:
Hover over any links in the email to see the actual destination URL. Avoid clicking on suspicious links, even if they appear from a trusted source.
Verify Information Independently:
If an email claims an issue with your account, contact CrowdStrike directly through trusted channels like their official website or known phone numbers.
Report Phishing Attempts:
Reporting suspicious emails to CrowdStrike and your email provider helps track and shut down phishing campaigns, protecting others from similar threats.
Beyond This Incident: Building Phishing Resilience
The CrowdStrike phishing wave is a stark reminder of the constant vigilance required in today’s digital landscape. Here are additional steps to build resilience against phishing:
Security Awareness Training:
Regularly educate yourself and your employees on recognizing and responding to phishing attempts. This training should cover the latest tactics used by cybercriminals.
Enable Multi-Factor Authentication (MFA):
Adding an extra layer of security to your accounts can make it significantly harder for attackers to gain access, even if they have your password.
Keep Software Updated:
Regularly updating your operating systems, browsers, and antivirus software ensures that known vulnerabilities are patched, reducing the risk of exploitation.
Be Wary of Attachments:
Avoid opening attachments from unknown or untrusted senders. Even seemingly harmless files can contain malware designed to compromise your system.
Lessons Learned and Moving Forward
The CrowdStrike outage, while disruptive, provides valuable lessons for individuals and organizations. It highlights the importance of having robust contingency plans and underscores the need for continuous vigilance against cyberattacks. By staying informed, practicing caution, and implementing real-time endpoint security, we can better navigate the ever-evolving threat landscape and avoid becoming victims of phishing scams.
Cybersecurity: A Shared Responsibility
Cybersecurity is not just the responsibility of tech companies; it is a shared responsibility of every user of digital technology. Together – sharing information, reporting suspicious activities, and adhering to best practices – we can create a more secure digital environment for everyone.
The CrowdStrike incident reminds us that no system is infallible. However, from global outages and continually improving our threat intelligence, we can mitigate risks and enhance our resilience against future threats. Stay informed, stay vigilant, and prioritize cybersecurity in your digital interactions.
In conclusion, the recent CrowdStrike IT outage and the subsequent phishing wave serve as a wake-up call. They remind us of how cybersecurity plays out in our interconnected world and the importance of being prepared for the unexpected. With the advice outlined in this blog and remaining ever-watchful, we can protect ourselves and our organizations from the relentless tide of cyber threats.