Dangers of Letting Neighbors Borrow Your WiFi
By Leo Notenboom
I have a home network with three computers (two desktops connected with ethernet cables to a Linksys router; laptop is wireless). The wireless signal is encrypted and I gave my next-door neighbors my network key so they can wirelessly connect just to check email, do banking, etc. They are not on my home network, but can they still see where I am surfing (such as my bank site with passcodes, etc.)?
•
Let me, at least, make one important correction to what you’ve described:
If you give someone access to your wireless access point, you have given them access to your home network.
They’re on it.
Now, what they can see depends on a number of things but to be blunt…
I hope you trust them.
•
A Wireless Connection
It’s important to realize that a wireless connection – regardless of how your hardware is set up – is a connection to your network.
A very common scenario looks like this:
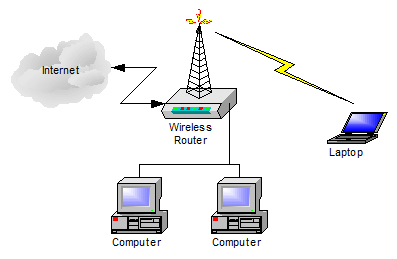
That’s a simple setup where multiple computers are connected to the internet via a single device: a wireless router. Some computers are wired, and some computers are connected via the wireless connection.
It’s important to realize that this is exactly equivalent to this:
A wireless router just puts the wireless access point in the same box as the router itself, but in either case it’s nothing more than a connection to your local network.
And of course machines on your local network should all be able to “see” each other.
About That Encryption
It’s good that your wireless access point is using encryption, but it’s important to realize what it does and does not do.
By giving your neighbor the password you’ve given them the encryption password. As a result, the encryption is not affecting your security with respect to them at all. It’s as if they were connected directly to your network – because they are. It’s almost the same thing as having given them a wired connection to your router.
The encryption prevent others – people to whom you have not given the password – from accessing your network.
But that’s all.
This post is excerpted with permission from Leo Notenboom.



