Upon evaluating the state of eight federal agencies’ digital infrastructures through a cybersecurity audit, it was confirmed, four agencies nearly failed. Had this been the first cybersecurity audit of those agencies, the scores may not be as alarming. However, in 2018 a similar audit was conducted exposing many of the same cybersecurity risks. The reality is, very little progress has been made.
Cybersecurity Audit Results
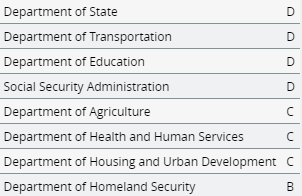
The scores, reported by Ars Technica, do not compare those to the audit of 2018; however it is clear little progress has been made in at least four of these agencies. The audit confirmed many of the departments using legacy Microsoft operating systems that are no longer supported. This means, they are not using Windows 10. All other versions of the Windows operating systems, (XP, Vista, 7, and 8) are no longer supported. Additionally, the audit revealed thousands of accounts remaining active, some for over 150 days, after an employee left, retired or was fired from the agency.
Moving Forward
Most certainly the auditors provided next steps for the agencies, in order to achieve a better score and increase their levels of compliance to best practices. However, it can also be assumed those same, or very similar, recommendations were provided in 2018. PC Matic founder and CEO, Rob Cheng states,
“The American government has placed a heavy emphasis on finding the responsible parties for the high-profile attacks that have taken place recently. Alternatively, it is suggested they focus on closing the security holes within our federal agencies to reduce the risk of attack. The audit clearly reports there are security holes from outdated operating systems, to improper access. I’m certain if they dug deeper, they would find holes in the cybersecurity software as well. It is imperative to close these holes to reduce the threat landscape.”
Closing the Holes
To close these holes, federal agencies need to update their operating systems to the latest version of Windows 10. It is also equally important to update any other outdated third-party applications. Additionally, it is important organizations follow the proper termination of employment policies. This may include, but is not limited to:
- Turning off employee access to the building
- Removing access to company networks
- VPNs
- RDP access
- Email accounts
- Social media
Removing employee access from the network should be rather simple, if proper records are being kept. For each employee, there should be documentation stating what they have access to. This enables the access removal process to be expedited. Additionally, when email access is removed, those emails should be forwarded to the individual’s supervisor. This will ensure minimal correspondence falls to the wayside after the employee is no longer with the agency.
Additionally, when it comes to cybersecurity solutions, it is just as important to ensure only trusted applications are allowed to run within the network. Federal agencies can achieve this by following their own advice, and implement a layer of application whitelisting within the existing cybersecurity stack.
Given the recent threats the private and public sectors have faced, it is imperative that each of these organizations heeds the advice of this audit. Cyber threats are growing. It is no longer a minor virus that may worm its way into the network. It is data breaches, ransomware, and in some cases, a combination of the two. The American government must do more to close its security holes instead of trying to track down the origin of the attack.
It’s imperative in order to secure the nation’s secrets, and the data of its citizens.