Cyberattacks pose a growing threat across industries, but operational technology (OT) environments face unique security challenges. Unlike IT networks, which benefit from traditional antivirus solutions, OT systems often operate on legacy infrastructure, prioritize uptime, and have limited connectivity. As a result, standard cybersecurity tools fall short in protecting these critical systems.
At PC Matic, we recognize these challenges and offer a proactive security approach tailored for OT environments: application allowlisting. This strategy isn’t just an alternative to antivirus—it’s a paradigm shift in cybersecurity, offering superior protection against zero-day exploits, advanced persistent threats (APTs), and unauthorized software.
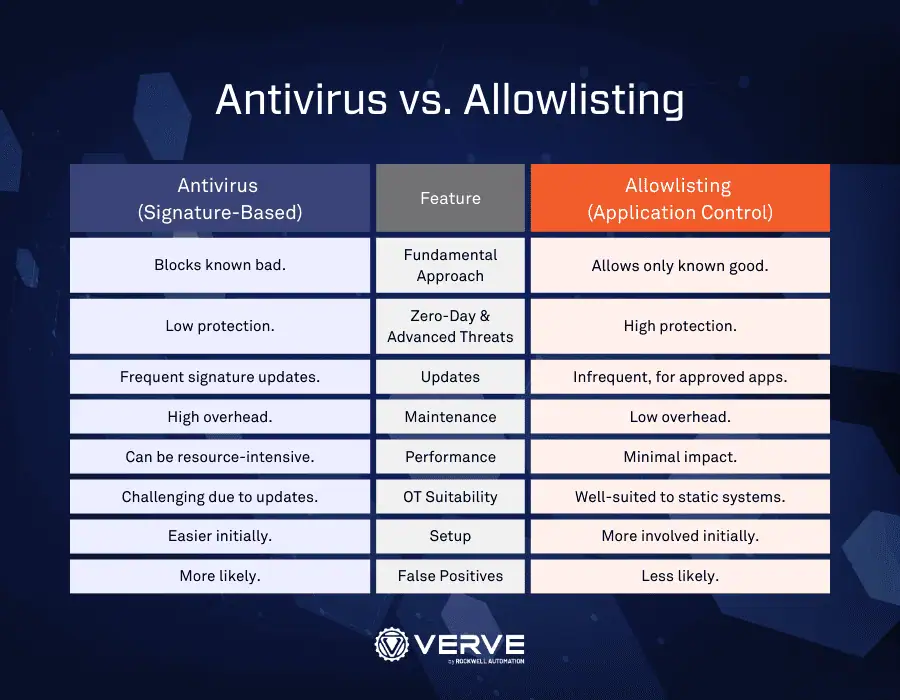
The Shortcomings of Traditional Antivirus in OT
While antivirus software is essential for IT networks, it fails to meet the demands of OT environments due to:
- Static Systems: Many OT systems run legacy software that cannot handle regular updates or resource-heavy antivirus scans.
- Limited Connectivity: Air-gapped or isolated OT networks make it difficult to receive frequent signature updates, reducing the effectiveness of traditional antivirus.
- Operational Disruptions: Antivirus scans can interfere with real-time processes, causing potential system failures or downtime.
- Reactive Approach: Antivirus software primarily detects known threats, leaving OT environments vulnerable to emerging zero-day attacks.
Given these limitations, organizations must shift toward a prevention-first approach to security. That’s where PC Matic’s allowlisting technology comes in.
What is Application Allowlisting?
Application allowlisting is a proactive cybersecurity strategy that permits only trusted applications to run while blocking all unauthorized programs by default. This approach aligns perfectly with the stability and predictability required in OT environments.
As explained by Verve Industrial Protection, “Allowlisting is a proactive cybersecurity strategy that blocks unauthorized programs from running by allowing only pre-approved applications to execute. It operates on a ‘default deny’ principle, meaning anything not explicitly permitted is automatically restricted.” (Verve Industrial)
The Benefits of PC Matic’s Allowlisting Solution for OT
- Prevention Over Detection: PC Matic blocks unauthorized applications, preventing malware and zero-day threats before they can execute.
- Minimized Attack Surface: PC Matic restricts software execution to only necessary applications, reducing entry points for attackers.
- Operational Continuity: PC Matic ensures system stability by preventing unauthorized changes or software installations.
- Regulatory Compliance: PC Matic supports industry standards such as NIST, IEC 62443, and NERC CIP.
- Alignment with Zero Trust Security: PC Matic enforces the principle of “never trust, always verify” to enhance security across OT systems.
How to Implement Application Allowlisting in OT: A 5-Step Process
Deploying allowlisting requires careful planning and execution. Here’s a streamlined approach to secure your OT environment using PC Matic’s proven deployment strategy:
Step 1: Planning Your OT Deployment
- Know Your Environment: Start with a full asset inventory—device names, IPs, OS versions, software, and criticality—to understand what needs protection.
- Choose the Right Tool: Select a solution like PC Matic that integrates easily and delivers strong security with minimal performance impact.
- Deploy with Confidence: Use remote tools like Active Directory or schedule on-site installs as needed. Engage OT teams early, follow change management protocols, and begin with soak testing on non-critical systems.
“Creating a comprehensive deployment plan is essential,” notes Verve Industrial. This includes a detailed asset inventory, compatibility assessment for older systems, and evaluating the performance impact of allowlisting agents.
Step 2: Deploy with Precision
- Start Small: Begin with a phased rollout—deploy PC Matic to a few systems first using a “low and slow” approach to reduce risk and network strain.
- Test First: Whenever possible, simulate your OT environment to test configurations before full deployment—minimizing surprises in production.
“Creating a comprehensive deployment plan is essential,” Verve explains.
Step 3: Simulate with Visibility and Insight
- Enable Visibility: Enable PC Matic’s Fingerprint Dashboard to include installed software details in scheduled scan reports. This feeds valuable data directly into the PC Matic Fingerprint Dashboard.
- Analyze & Collaborate: Use the Fingerprint Dashboard to identify active applications, review file details, and collaborate with OT teams to validate legitimate use and flag anomalies.
This phase is crucial for “building an accurate allowlist,” Verve explains, and typically lasts a few weeks to capture normal operational activity.
Step 4: Review and Allow
- Review & Refine: Use the PC Matic Fingerprint Dashboard to review discovered applications and define what should be allowed.
- Handle Unsigned Apps: Evaluate custom or unsigned applications carefully. Once verified, allow them by vendor, product, or specific application to maintain security without blocking legitimate tools.
Verve highlights the importance of using a layered approach—publisher-based, path-based, and hash-based—to balance flexibility with security.
Step 5: Lock Down with Confidence
- Phased Enforcement: Start by locking down “soak test” systems, monitoring closely for any blocked applications or alerts.
- Adjust & Expand: Fine-tune your allowlist as needed, then gradually expand lockdown across all systems using the proven “low and slow” approach.
- Stay Proactive: Regularly review logs and rules. Unlike reactive tools, PC Matic’s allowlisting anticipates and blocks threats before they reach critical systems—ensuring stronger security, compliance, and uptime.
“Once the allowlist is validated on the test systems, gradually roll out the lockdown to the remaining systems, following the ‘low and slow’ approach,” advises Verve.
Addressing Common Concerns About Allowlisting
Organizations often hesitate to implement allowlisting due to concerns about complexity, potential disruptions, and maintenance challenges. However, PC Matic’s allowlisting solution addresses these challenges with:
- Simplified Deployment: PC Matic’s automated tools and centralized management ease the transition.
- Minimal Operational Impact: A carefully planned rollout with PC Matic ensures zero downtime.
- Cost-Effectiveness: Preventing a single cyberattack with PC Matic can save millions in downtime and damages.
- Effortless Updates: PC Matic’s trusted directories allow for seamless patching and software updates.
As Verve states, “While initial setup requires planning, modern allowlisting tools offer automation features and centralized management consoles to simplify ongoing maintenance.”
Why OT Organizations Must Act Now
The cyber threat landscape is constantly evolving, and OT environments cannot afford to rely on reactive security measures. Implementing application allowlisting with PC Matic is a decisive step toward fortifying critical infrastructure, ensuring operational resilience, and staying ahead of emerging threats.
The question isn’t whether to adopt allowlisting—it’s how soon you can implement it. Don’t wait for a breach to take action. Strengthen your OT security today with PC Matic’s advanced application allowlisting technology.
Source: Verve Industrial Protection: 5 Steps to Successful Whitelisting Deployments in OT




