Microsoft Exchange New Release is Vulnerable.
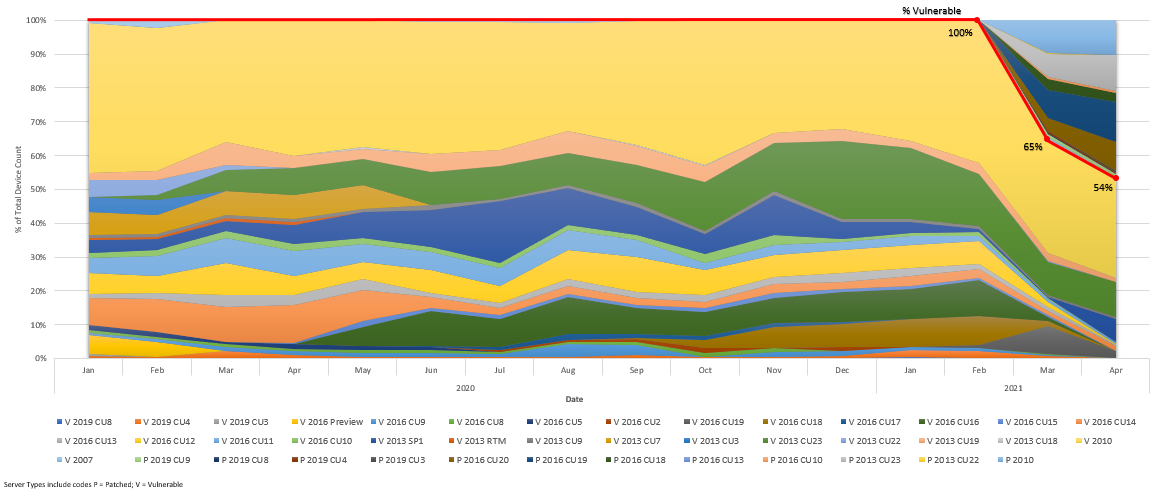
In mid-March, we issued a guide to the patching of vulnerable versions of Microsoft Exchange Server. The affected versions include Exchange Servers 2010, 2013, 2016 and 2019. In mid-April, we took a look at our data to see how quickly users are updating this software to the new releases. Unfortunately, we’re not seeing as much progress as we anticipated regarding the Microsoft Exchange vulnerable release. Remarkably, our data shows that more than 50% of devices are still running vulnerable versions.
What Component is Vulnerable?
The vulnerable MS Exchange component is part of the network stack. The set of possible attackers extends beyond those normally listed to the entire Internet. This type of cyber-vulnerability is often termed “remotely exploitable“. This makes a cyber attack at the protocol level possible across one or more routers. To ensure greater cyber-protection, users should check to see that they aren’t running vulnerable releases of the program.
Security is proposedly one of the main benefits of using Exchange Server. It allows users to link their email, contacts, and calendars from Windows applications on their PC to browsers, and to their mobile devices. IT administrators should prioritize installing updates to help protect users’ confidentiality. The vulnerability patch will help prevent a loss of confidentiality which could result in data being divulged to an attacker.
PC Matic is confident that its customers are secure but stresses that any vulnerable software should be patched immediately as a best practice. As new releases of Microsoft Exchange come out, our team of cyber security specialists will continue to monitor vulnerabilities.
Visit the Microsoft Download Center to download new releases.