By Bill Pytlovany
Preventing a Crippling Cryptolocker Extortion Attack
A common example of how Cryptolocker is infecting computers.–PC Pitstop
A common way computers are infected or compromised has always been a simple yet well thought out deception. It can happen to anyone and the use of social trickery is nothing new. Understanding the victim is all that’s needed to receive their cooperation.
If you’re thinking it could never happen to me this refresher couldn’t hurt. You might want to share the examples here with your friends, family and especially your employees. Social engineering has come a long way since the possibility of seeing Anna Kournikova naked.
Here’s a common example that has been used to infect computers with the crippling Cryptolocker extortion attack.
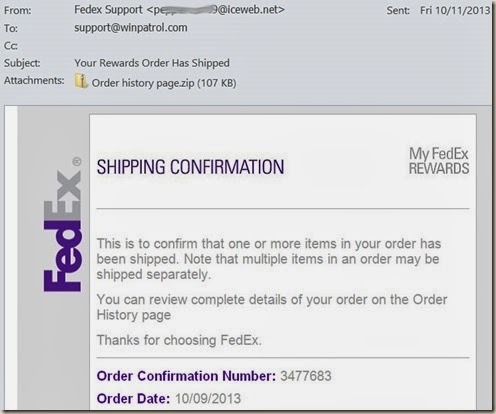
This one and variations are going to get more popular as Santa starts shipping his presents. In this example the “From” email isn’t even disguised which means these guys were really lazy. Don’t bother replying because the Email address belongs to someone who has already been hacked and was probably shut down by the time you receive your Email.
This post is excerpted with Bill’s permission from his blog
Note to PC Matic users: Because PC Matic’s security, called Super Shield, uses a white list and a black list, you are protected from ransomware like Cryptolocker, but you have to make sure Super Shield is properly enabled. We are getting reports of PC Matic users becoming infected because they have not enabled Super Shield. It is not hard to know. Just look at the tray icon and the Super Shield logo should be present and green.




