What actually is ransomware?
We’ve all heard about ransomware and the attacks on governments, schools, and businesses. It seems like ransomware is everywhere. But what is it exactly? What does it do? What does it looks like? Let’s explore this ever growing threat so we can better understand it.
A definition
I hear a lot of people telling me they want to protect themselves against ransomware and malware, but they’re the same thing. Ransomware is a form of malware.
Malware is created for nefarious purposes and is short for Malicious Software. It can include ransomware, but also viruses and spyware. A virus can do major damage to your machines and files. Spyware can watch you like a peeping tom through your window at night. Ransomware is just as the name suggests, software that holds you ransom.
What does it do?
Ransomware can enter your machine a number of different ways; phishing scams you click on yourself, open RDP, and brute force to name a few. Once inside, the code races through your files, encrypting them and making them inaccessible to you.
What does it look like?
When you have a ransomware infection, you will know.
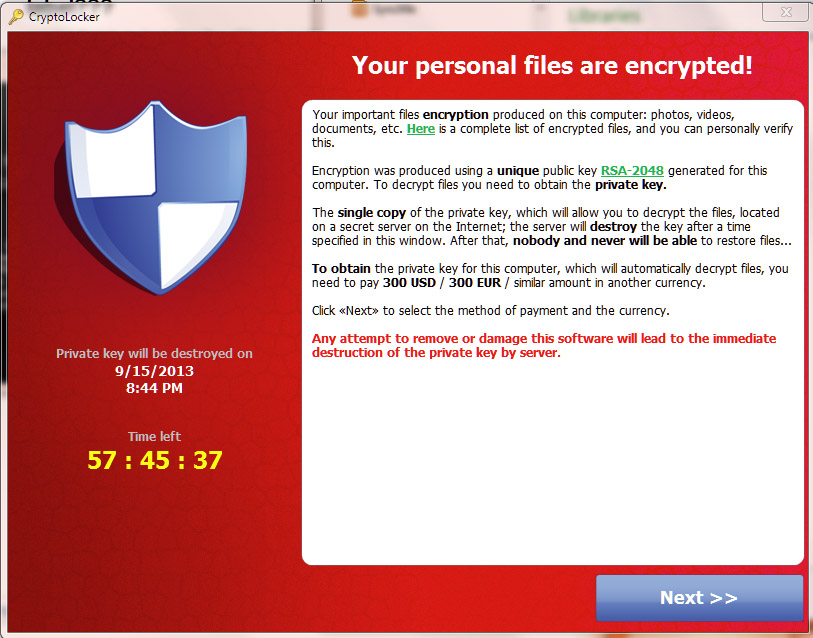
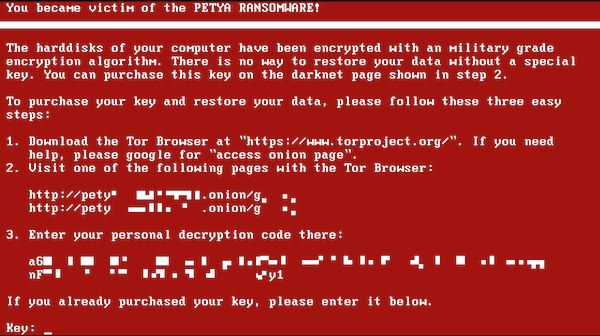
There is always a message, usually presented as a complete takeover of your screen, to let you know what’s just happened. The messages come in different forms and styles, but the idea is always the same.
You’re informed of the ransomware takeover and given instructions on how to purchase the decryption key.
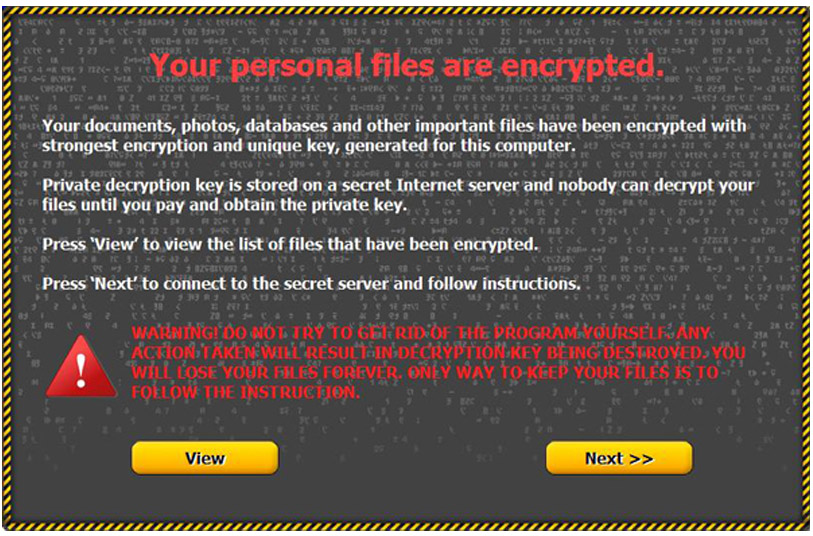
Bitcoin is the preferred method of payment due to it’s inability to be traced. Once the ransom is paid, there’s only a 50/50 chance the decryption key will be sent.
How fast does it work?
As with any software program, individual code runs differently. There are strains that hang out in your hard drive for days, taking their time to wind through your files until it has a grasp on everything. This is also effective if the attacker is waiting for you to plug in a backup device. While laying dormant, the strain can wait for the device to be plugged in then encrypt that as well.
Many are less patient though. Ransomware can take hold in a matter of seconds, forcing a system failure and then the ransom page on reboot. All it takes is to click a link or open an attachment and they have you before you can even call tech support.
Who are the targets?
Unfortunately, small business and higher education seem to be the most frequent targets of ransom attacks. Both tend to have smaller IT staff and more users which ups the likelihood of someone making a security error.
As attackers, and subsequently the strains of ransomware they use, become more sophisticated, larger corporations and government entities are finding themselves the victims of more frequent attacks. The relatively low risk is more than worth the potential reward of undertaking these more complicated projects.
What to do?
As we’ve said before, application whitelisting is the future of ransomware protection. It’s being recognized more and more by governing bodies as the only effective solution in the prevention of ransomware.
Education is hand in hand with proactive approaches to security. Knowing what a phishing scam looks like, being wary of unsolicited (and solicited) files, and being diligent in spotting abnormalities will all reduce the risk of human error.