Ransomware Crooks Offering “Customer Service”
UPDATE: 11/14/2013
The CryptoLocker Decryption Service allows victims to check the status of their “order” (the ransom payment) and complete the transaction. I am not making this up!
Those who paid the ransom (with either Green Dot cards or Bitcoins), but did not get the decryption key — or got one that didn’t work — can download it again.
Those who missed the 72-hour deadline can also get their key, but the price jumps from two Bitcoins to 10. At today’s market value, that’s nearly $4,000. And Green Dot is not accepted with this extended-deadline service.
—CryptoLocker crooks launch new ‘customer service’ website for victims | Herb Weisbaum | NBC News contributor.
More info:
CryptoLocker Crew Ratchets Up the Ransom–krebsonsecurity.com
BleepingComputer.com CryptoLocker Ransomware Information Guide and FAQ
10/18/2013
Ransomware 2.0 Comes to America
by Rob Cheng
This month, we were in Berlin for the VB100 and there was a presentation about Ransomware. As reported earlier this year, ransomware is alive and well in the US in the form of the DOJ and FBI viruses. The news is that the virus mafia has created a new version of ransomware more treacherous than the DOJ and FBI viruses. Instead of locking the computer and demanding payment, the virus first encrypts important files on the target computer, and then demands payment not for the computer but the data. At the time, the researchers reported that the virus was isolated to Russia. As soon as we returned from our trip, I discovered that our researchers had found the virus in the United States.
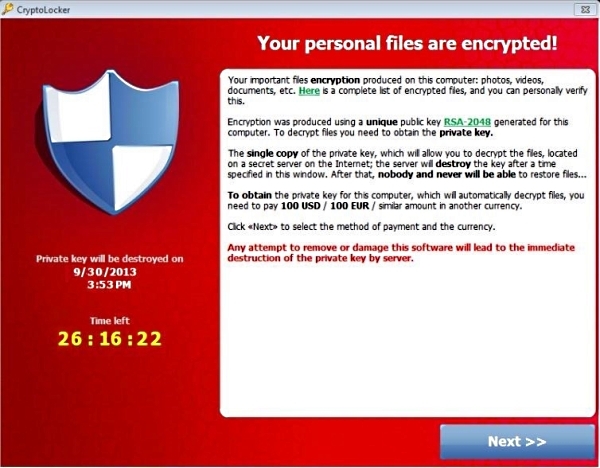
We have checked our statistics and we have found at least 6 instances of ransomware in the month of September alone. The binary is not signed nor is the vendor or product fields populated. We refer to these viruses as anonymous. The file names appear to be random characters that are either 4, 15 or 16 characters and the file size varies and hovers around 300K. The only telling sign is that it installs in the roaming directory as opposed to one of the Windows or browser temporary directories.
We ran the virus on a test machine and before it delivers it messages, it spends hours encrypting files. The virus ranges from 0 to 50% processor utilization and the hard drive light is blinking although not pegged. During this time, it is possible to continue normal operations although performance suffers. Once the encryption process is finished, it delivers its payload.
I have talked to technicians in various parts of the US and they all know that there is a new threat upon us. Unfortunately once the computer has been infected and the files have been encrypted, there is little technicians can do. This is different than ransomware 1.0, or other strains of viruses. Prior to ransomware 2.0, if you have been infected, security software could remove the virus, and restore normal operations of the computer. In the security business, we call it remediation. With ransomware 2.0, there is no way to remediate the encrypted files. Worse yet, if the virus is removed from the system, there is no way to pay the ransom, so the files at that point are lost forever.
 Make sure the Super Shield logo is present and green in the system tray to avoid Ransom Ware.
Make sure the Super Shield logo is present and green in the system tray to avoid Ransom Ware.I hope this is a wake up call for the entire security industry. The industry has been over focused on remediation instead of prevention. The only solution for ransomware 2.0 is to make sure the viruses never runs on the target machine. Remediation is futile.
Ransom ware 2.0 is a polymorphic virus which means that it escapes the traditional black list detections.
Note to PC Matic users. Because PC Matic’s security, called Super Shield, uses a white list and a black list, you are protected from ransomware, but you have to make sure Super Shield is properly enabled.
Video: Step by step instructions for how to install and enable Super Shield.




