The Advantages of White Listing to Computer Security
by John McKenna – PC Matic
The Advantages of Application Whitelisting to Computer Security. Years ago, a CEO’s primary concerns were profitability, brand awareness, operational efficiency and employee and customer satisfaction. An important list for any CEO but in today’s business environment, the list has grown. Technology, government intervention, compliance and global events have resulted in other critical concerns for a CEO and rightfully so.
Compliance issues can cost a company millions of dollars in penalties and a breach of security could be equally damaging to a brand and the bottom line.
Security software is a $20 billion dollar industry and what is truly fascinating is that until now, nearly every company offering a security software solution uses the same process or concept. With all the technology advancements in today’s world, why is it only one company, PC Pitstop, has re-engineered the security software process?
Cybercriminals are Adapting All The Time
Cyber criminals are changing the landscape every day and creating new viruses, yet every company, except PC Pitstop, has continuously used the same approach to security software. This antiquated approach is still somewhat effective but it is clearly not leading edge. Instead of being innovative, like PC Matic, most security software companies are like lemmings, they follow rather than lead.
PC Matic is a leading edge company and unlike its competitors, they have made the appropriate investments. The end result is a suite of software products such as PC Matic PRO, Endpoint Security Software for business and enterprise, Ransomware Protection, for government entities Federal Agency Security Software, and Server Security Software. These all use white-list technology making PC Matic PRO for a superior cybersecurity solution.
Most companies use a “black list” as part of their solution to provide security software. A “black list” is a “list” of all the known bad viruses. PC Matic PRO Security Software uses a “black list” on the back-end and a “white list” on the front-end. The “white list” is a list of all the good programs that are welcome on your computer or enterprise system.
I will use an analogy to easily demonstrate the new approach PC Matic has developed as compared to its competitors. The end result, PC Matic PRO, is a best-in-class solution for businesses concerned about security software.
The PC Matic pro-active approach to security software:
You are having a holiday party at your home and you create a guest list. Your guest list is the same as a “white list”. The names on the guest list are good friends or people you trust having in your home. You have a greeter at the door checking to see if the person is on the guest list. If they are on the guest list, they are welcomed into your home and they are free to roam around and enjoy the party.
If a person comes to the door, who is not on the guest list, they are not allowed immediate entrance and nor are they told to leave. They are asked to step aside and additional due-diligence is done to ensure they are a valid guest. Once that process is completed and it is a brief delay, the guest is either allowed entrance or asked to leave.
The competition’s reactive approach to security software:
They are also having a holiday party at their home and their greeter uses a “black list”, a list of people not invited to the festivities; similar to that of the “black list” with all the bad viruses. The greeter at the door verifies whether or not the guest is on the “black list”. If they are, they are asked to leave and not allowed entrance. If they are not on the list, they are welcomed in and are free to roam around and enjoy the party.
This may seem to be a subtle difference but it is significant. When a company uses a “black list” as their gatekeeper, they unknowingly expose themselves to bad viruses. New or unknown programs are not on the blacklist. Staying with the analogy, the “black list” poses serious risk because of the following:
Viruses Disguise Themselves
*A virus can disguise itself, also known as morphing, and gain access to your computer/system. It looked and acted like a good virus but actually it was a disguise and is now in your “home”.
Viruses Adapt and Change
*It is incredibly expensive and time consuming to try and stay current with all the known bad viruses. Cyber criminals are creating new viruses daily with the attempt to commit serious harm to our ecosystem. In fact, modern malware is able to penetrate a system using fileless methods, drop a viral payload. Once the payload is on the system, they delete their tracks making them harder to detect.
Blacklist Antivirus Can’t Keep Up
*The black list approach does not have the bandwidth to include all potential bad groups. An example would be our competitors allow entrance to a homeless person into their home. They were not on the “black list” but they have a high propensity to commit a crime.
Reaction vs Prevention
*Probably the most important risk is the “black list” is a reactive method, not proactive. A crime has to be committed prior to getting on the “black list”. Your company or home, as in the analogy, could be the first victim and we all know this could be devastating to a company or family.
Remember the world we live in today. Several of our top financial institutions have been robbed of over $1,000,000,000 dollars because of a bad virus that laid dormant in their system. Bonnie and Clyde could never get away with a billion dollar heist because it would take too long to carry out of the bank and they would need a humongous get-away vehicle. In today’s environment, this could happen at the blink of an eye.
Even Large Enterprises Can Be Targets
Target was a victim when a thief gained access to their customer’s credit card data and personal information. Both scenarios relied on the “black list” approach as part of their defense.
Think about this, in your personal life and in business, when is best time to approach a situation reactively? An illness, no! Paying your bills, no! A competitive advantage, no! Your strategic vision, no? Paying employees, no! So why would a company risk its reputation/brand and all its company data by using a reactive approach to defending against a software virus? It just does not make sense.
The Main Advantages of White Listing to Computer Security
With PC Matic, the approach is pro-active. A virus cannot gain access to a system because they use a “white list” on the front-end. This approach only allows valid software to gain access to your computer system. Any program not on the “white list” will be vetted prior to gaining access and verifying the digital signature associated with the software. This one of the main advantages of white listing to computer security for all organizations.
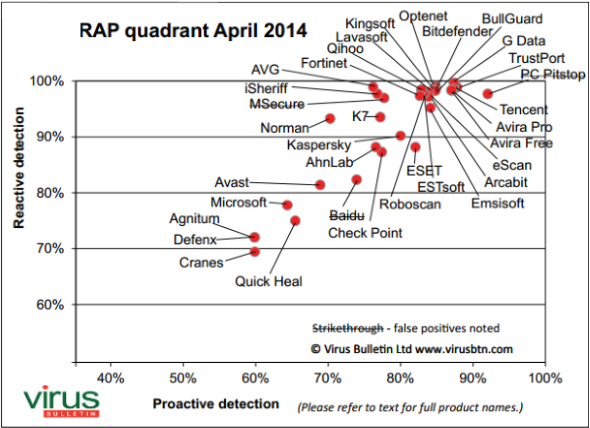
The two approaches are significantly different and yet only one company, PC Matic, has thought outside the box and is leading edge. To validate this approach, our company recently participated in a free, non-biased test conducted by Virus Bulletin. Being free, a company cannot influence the outcome by “investing” more money on the testing company.
This test is all about facts and capability and PC Matic Security Software ranks number 1, with a 92% rating. No gimmicks; the grade a company receives is solely based on functionality and performance of their security software. Read more about computer security.
Security Software Company Comparison
Some believe the more money you throw at this problem, the safer they are but that is not even close to being accurate or a good business decision. Others believe you can never be safe and that too is inaccurate.
Even worse, some Executives believe “it will never happen to me!” Defending your company against a software virus can be achieved and it is not based on the amount of money you spend to defend your company, rather it is the capability and method your business partner uses to address this important issue.
“Safety is not a gadget but a state of mind.” Eleanor Evert
PC Matic Pro is Superior Software
PC Matic PRO is one of the best security software solutions using Application Whitelisting to stop malware and ransomware. Our computer and system protection using AWL is the superior solution and will enable a CEO to sleep at night.
This article discussed advantages of white listing to computer security. To learn more about PC Pitstop & PC Matic PRO e-mail John McKenna at [email protected] and he will follow-up with you immediately.