Modern cyber security is an ever-evolving, adaptive process. Because malware and other digital threats constantly change and improve, cyber security efforts, processes, and technologies must also improve and utilize layered security approaches, particularly when protecting large organizations. Many organizations and cyber security systems or technologies leverage cyber kill chains to accomplish their security goals.
Whether you’re an individual or representing a company, you need to know what the cyber kill chain is, how it works, and the benefits of implementing it in your cyber security approaches and practices.
The Cyber Kill Chain Explained
Put very simply, the cyber kill chain model is an adaptive model and step-by-step process that helps organizations track, understand, anticipate, and stop cyber threats of all types. The term “cyber kill chain” comes from the military term “kill chain,” which refers to a series of stages or steps needed to prepare, attack, and destroy targets.
Indeed, the cyber kill chain as a concept was originally developed by Lockheed Martin in 2011. Then and now, the cyber kill chain helps organizations outline different steps used in common cyber attacks in order to anticipate and stop them. More importantly, the cyber kill chain helps organizations determine which stages or areas of their organization they should protect or intercept attackers most frequently.
Note that the cyber kill chain is not a methodology by which cyber security teams and technologies operate. Instead, it’s a hypothetical sequence of steps that cyber attackers use to accomplish their goals. In theory, by better understanding the steps an attacker will use to acquire information or money, your security team will be able to stop them more effectively.
At its core, the cyber kill chain is meant to help organizations protect themselves against more sophisticated cyber attacks, including advanced persistent threats or APTs. APTs are particularly important to guard against since those who make them oftentimes spend a lot of time surveilling a target or planning an attack before it occurs.
Role of the Cyber Kill Chain in Cyber Security
The cyber kill chain can help your organization protect itself against all manner of cyber threats, ranging from Trojan viruses to malware to ransomware to spoofing attacks to social engineering attacks and much more. It does this by putting you in the mindset of a cyber criminal, such as a malware virus creator.
When leveraged and understood properly, the cyber kill chain will help you not only figure out how a potential attacker will likely gain entrance into your system, but it will also help you figure out the best or most effective security measures to implement.
For example, if you model the cyber kill chain and determine that an attacker will be most likely to try to get entrance into your system through phishing emails, you can then determine that the best defense is some combination of:
· Using more sophisticated firewalls
· Educating your employees to prevent them from opening unknown emails
· Requiring employees to swap out their email passwords frequently
· And so on
You can adapt this approach to any potential threat, like remote access viruses, scripting, denial of service attacks, and more.
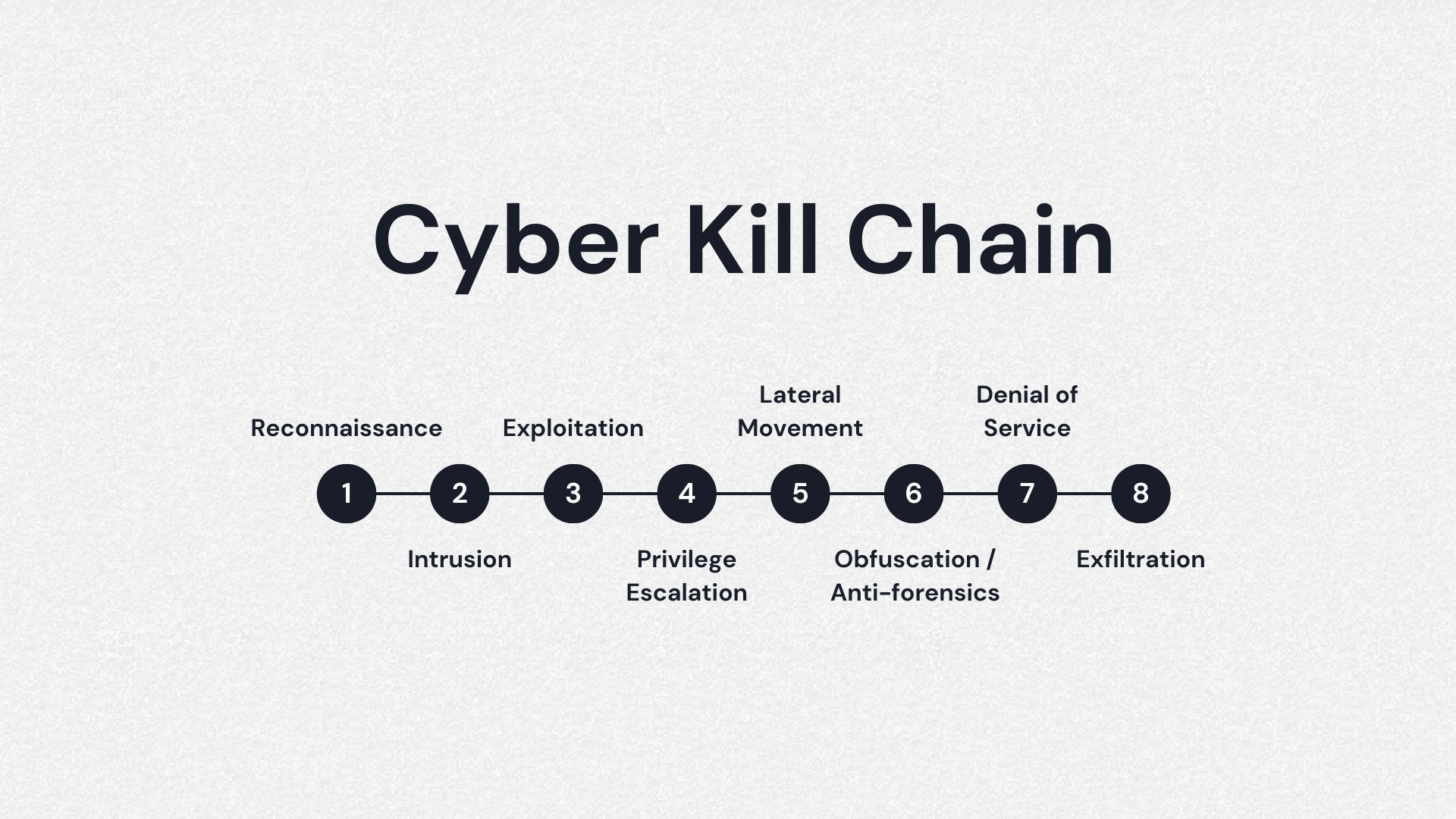
8 Phases of the Cyber Kill Chain Process
The cyber kill chain is comprised of eight primary stages, although the original Lockheed Martin cyber kill chain only had seven steps. Here’s a breakdown of each phase one by one:
· Phase 1: Reconnaissance. In this phase, the cyber criminal collects data and information about the target and prepares for the attack. For example, the attacker may gather email addresses, passwords, IP addresses, and much more. More sophisticated attackers may also scan firewalls and try to identify intrusion prevention systems, like cyber security software
· Phase 2: Weaponization. In this phase, the criminal then creates an attack vector or pathway. This is essentially choosing the virus or method by which they will gain entrance into the target system. The attacker might use malware, ransomware, another virus or worm, or even a phishing scheme to get access to the target system. In this phase, the cyber criminal can also set up “backdoors” to continue enjoying access to the system if the original entry point is closed
· Phase 3: Delivery. In the delivery phase, the cyber criminal launches their attack. For instance, if they choose malware, they send a malware virus via email or some other vector in order to gain access to the target system. In this phase, the criminal may combine their chosen attack virus with social engineering techniques, like posing as a maintenance technician
· Phase 4: Exploitation. In this phase, any malicious code or virus is executed within the target system for sensitive data theft, privilege escalation, and more
· Phase 5: Installation. In this phase, the attack virus, like a malware virus or ransomware virus, is installed on the victim’s system. This usually allows the attacker to assume control of the target network or system and begin operations
· Phase 6: Command and Control. In the Command and Control phase, the attacker uses their malware or other malicious code in order to assume control of a device or target network. The attacker may begin their core goals or move laterally throughout the network, expanding to other terminals or computers connected to the same network overall
· Phase 7: Actions on Objective. In the penultimate phase, the attacker starts to carry out whatever their intended goals might be, such as destruction, data theft, exfiltration, encryption, and blackmail
· Phase 8: Monetization. This phase is not a part of the original Lockheed Martin cyber kill chain. However, it’s often considered to be an important phase in modern threat analysis. In this phase, the cyber criminal tries to get income from the attack, such as demanding a ransom be paid in Bitcoin after delivering a virus to a target network
How the Cyber Kill Chain Works
The cyber kill chain works by allowing cyber security teams or individuals to better understand the methodologies and mindsets of cyber criminals. In the phase breakdown above, cyber security teams or individuals can visualize how a potential cyber criminal might attack a target system.
Once they understand how a potential criminal might attack a system, they can erect defenses that are designed to protect the easiest or most vulnerable entry points.
How Do You Effectively Use the Cyber Kill Chain?
Understanding the cyber kill chain is one thing. Being able to effectively leverage and utilize it is another.
Effectively using the cyber kill chain means looking at each stage and implementing different layers of control or security depending on what works best. Generally, those who use the cyber kill chain to understand cyber criminals use six different types of security controls:
· Detection, in which the security team tries to detect or determine attempts to penetrate a system or organization
· Denial, in which the security team or software stops attacks as they occur
· Disruption, in which the security effort intervenes in data communication performed by the attacker to stop an attack in process
· Degradation, in which the security effort limits the effectiveness of cyber security attacks and minimizes any ill effects
· Deception, in which the security effort misleads an attacker by giving them false information or directing them to a false terminal
· Containment, in which the security effort contains and limits the attack scope so it doesn’t do as much damage to a whole organization
Different measures may be more effective at different stages of a cyber attack.
For example, if a criminal is in the Reconnaissance phase of the cyber kill chain, the best antidotes or security methods are detection and denial. Detection may be carried out by threat intelligence organizations or by leveraging a network intrusion detection system. Alternatively, a security team might practice denial; they might implement an information-sharing policy for all organizational employees or use very strict firewall access control lists.
What if the criminal is at another stage in the cyber kill chain? Say that they are in the Delivery phase. In that case, the security team might use detection through endpoint malware protection in order to prevent a malware virus from being delivered in the first place. Or they might use denial by changing management, using a proxy filter, or using a host-based intrusion prevention system.
In any case, the cyber kill chain enables cyber security teams to choose the best security approaches or countermeasures based on what they think is happening (or is about to happen).
Benefits of the Cyber Kill Chain
The cyber kill chain is very beneficial for organizations and individuals alike.
When leveraged properly, it enables cyber security teams and software to be more effective, improving their value and minimizing the effectiveness of cyber attacks. Furthermore, it can result in more cost-effective software or security tools. For example, a costly but comprehensive cyber security software suite is only effective if you use it properly. The cyber kill chain framework can help you do just that.
In addition, the cyber kill chain framework serves as an effective educational tool for beginners to cyber security topics in general. In essence, the cyber kill chain helps teach beginners how cyber security breaches occur and how cyber attacks are most likely to affect an organization. Because of this, the cyber kill chain is often one of the earliest frameworks taught to new cyber security students or workers.
What is the Difference Between the Cyber Kill Chain and the MITRE ATT&CK Framework?
Both the cyber kill chain and the MITRE ATT&CK or Adversarial Tactics, Techniques, and Common Knowledge frameworks are useful. But there are some core differences between both approaches.
Both of these are frameworks that cyber security teams used to understand their adversaries and anticipate cyber attacks. But while the cyber kill chain framework looks at cyber threats from a high-level perspective and has seven or eight distinct phases, the MITRE ATT&CK framework incorporates much deeper knowledge with granular details about specific cyber attacks.
Basically, the cyber kill chain assumes that all cyber attacks follow a specific and similar sequence of attack tactics or steps in order to achieve their goals. In contrast, the MITRE ATT&CK framework is a more comprehensive knowledge base that uses environment-specific MITRE ATT&CK cyber security information with hierarchies of tactics and techniques to let security personnel better anticipate and protect against specific attacks/virus types.
Both approaches can be beneficial for your organization, and you may wish to implement both depending on the task at hand. The cyber kill chain is better for beginners, as it offers simplicity and a foundational understanding of cyber attack processes.
The MITRE ATT&CK is a little more comprehensive and better for experienced cyber security analysts or teams. In this way, MITRE ATT&CK is much more useful to threat hunters or “red teamers,” as well as anyone who designs and implements new security controls or policies, like network architects and administrators.
Wrap Up
As you can see, the cyber kill chain is an important and adaptable framework that allows organizations to trace cyber attack stages, identify vulnerabilities ahead of time, and assist with cyber security efforts. It’s an integral part of modern cyber security technologies and systems, so you should leverage it in your business starting today.
Technologies like PC Matic can help you accomplish the various stages in the cyber kill chain. For example, PC Matic Pro offers proactive security and remote management services to help you stay ahead of and stop cyber threats. Contact us today to learn more.