Your organization needs high-quality, responsive cyber security. But to achieve and maintain good cyber security practices and results, you need to leverage in-depth, comprehensive security frameworks like the MITRE ATT&CK framework. Read on to learn more about the MITRE ATT&CK framework, what it means, and how to leverage it for greater security results.
The MITRE ATT&CK Framework Explained
Put simply, the MITRE ATT&CK framework is a comprehensive and in-depth knowledge base and model for cyber attacks and cyber criminal behavior. It reflects different phases in a cyber criminal’s attack or the phases in a malware attack, as well as explains the platforms that such attacks are most likely to target.
“MITRE ATT&CK” stands for MITRE Adversarial Tactics, Techniques, and Common Knowledge. It abstracts tactics and techniques and offers a framework or taxonomy for individual cyber criminal actions.
Think of it this way: the MITRE ATT&CK framework is a guide that cyber security personnel can use to better understand cyber criminal efforts and likely attack patterns. By understanding how a cyber attack is likely to occur in the future, a cyber security team can better anticipate or stop that attack in the future.
The MITRE ATT&CK framework or behavioral model is broken down into three core components:
· A series of tactics that show the short-term and tactical goals that cyber criminals use during an attack. These are the columns in the MITRE ATT&CK matrix (see more below)
· A series of techniques that tell cyber security teams how adversaries achieve their tactical goals. These are the individual cells in the MITRE ATT&CK matrix
· Documentation for cyber criminal usage of different techniques plus metadata. This tells cyber security teams how frequently certain approaches or technologies are used
With the MITRE ATT&CK framework, your organization can protect itself against endpoint viruses, malware sub-techniques, spear phishing, and all other types of digital threats. It’s an important part of damage mitigation and cyber threat intelligence throughout any business or product lifecycle.
The MITRE ATT&CK Matrix
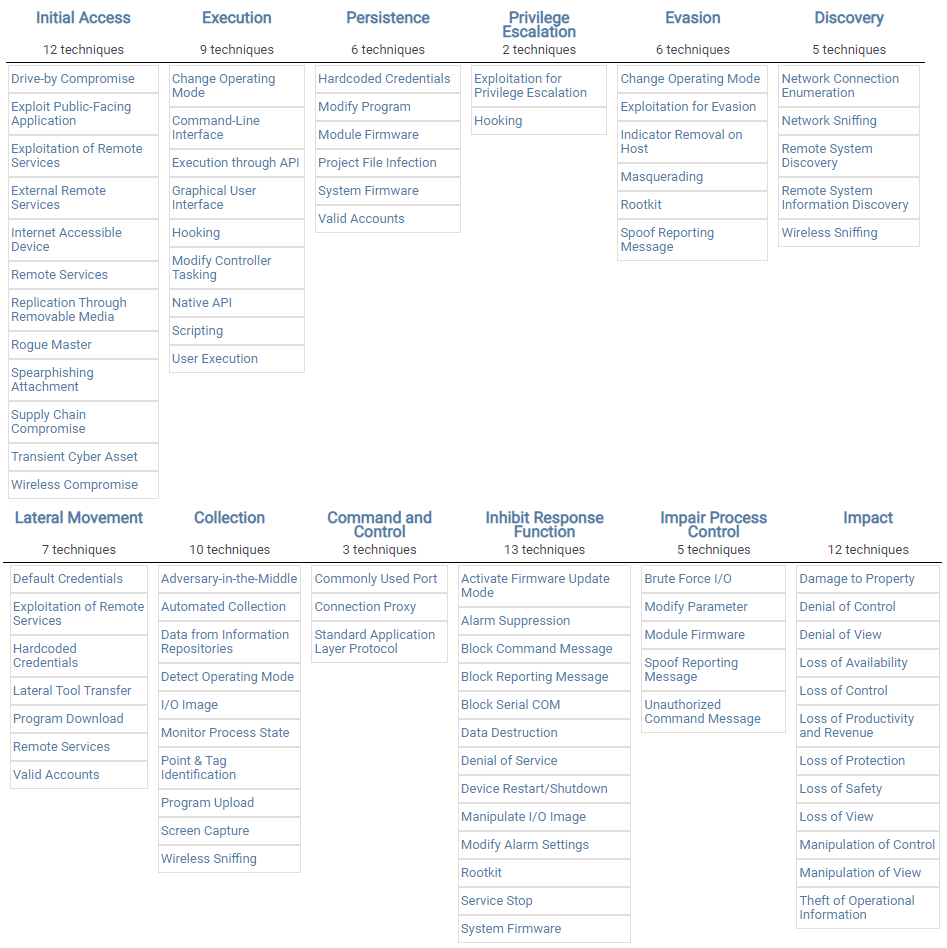
The MITRE ATT&CK matrix is the chart which cyber security personnel can read to understand different adversarial actions and techniques. It catalogs information and correlates different adversary groups to “campaigns.” Put more simply, the MITRE ATT&CK matrix categorizes different tactics and techniques with each other so that cyber security teams can better understand how they need to direct their efforts.
The MITRE ATT&CK matrix is a chart of columns and cells, similar to the chart on a Microsoft Excel document. The top row of cells dictates the MITRE ATT&CK tactics that could be used by a digital adversary and denote different columns. In each column in the cells beneath the first row, cyber security personnel will find different techniques assigned to each tactic.
Let’s take a closer look at MITRE ATT&CK matrix tactics and techniques now.
MITRE ATT&CK Tactics and Techniques
The MITRE ATT&CK framework breaks down both cyber criminal tactics and techniques, which are not the same things. The MITRE ATT&CK tactics are the short-term strategies or objectives that cyber criminals will execute in pursuit of their goals. There are 14 MITRE ATT&CK tactics currently recognized by the framework, and they are:
· Reconnaissance, or gathering information to plan future cyber criminal operations
· Resource development, during which the cyber criminal gets resources to support its operations. For example, the adversary might create a new malware virus
· Initial access, during which the adversary tries to get into the target network. For instance, the criminal might run a remote access tool or embed a malware virus in an email
· Execution, in which the criminal attempt to run malicious code
· Persistence, in which the adversary tries to maintain any foothold by changing configurations or by throwing cyber security personnel off their scent
· Privilege escalation. In this tactic, the adversary tries to get higher-level permissions in the target network. They may use a low-level vulnerability to elevate access to administrator or something similar
· Defense evasion, during which the adversary attempts to avoid being detected or kicked out of the target system through cyber security efforts. For instance, they might use trusted processes to hide malware viruses
· Credential access, during which the adversary steals account names or passwords in order to elevate access or for other purposes. They might use tools like keyloggers to do this
· Discovery. In this phase, the adversary attempts to figure out the target environment and determine what they can control or damage
· Lateral movement. In this phase, the cyber criminal moves through the target environment and uses legitimate or falsified credentials in order to move freely
· Collection, during which the adversary gathers data depending on their goal. For instance, they may gather target customer data and cloud storage if they wish to sell it to the highest bidder
· Command and control, during which the adversary communicates with compromised systems and controls them
· Exfiltration, during which the adversary steals data and/or transfers it to a separate cloud account or end terminal
· Impact. In the last phase, the adversary performs its final and impactful actions, such as destroying systems and data (by encrypting it with ransomware, for example), manipulating systems, or interrupting data transfers
To recap, there are 14 distinct MITRE ATT&CK tactics recognized by common cyber attacks. But for each tactic in the MITRE ATT&CK matrix, there are adversary techniques.
MITRE ATT&CK techniques described the activity carried out by the adversary more specifically. For example, in the “Execution” column or tactic on the MITRE ATT&CK matrix, cyber security personnel will find potential techniques such as:
· Dynamic data exchange
· LSASS driver
· Mshta
· PowerShell
· Execution through API
· Graphical User Interface
The techniques tell cyber security personnel how an adversary might achieve a tactic or objective. For example, to execute a virus, a cyber criminal might use a graphical user interface as an injection point for a malware virus.
The MITRE ATT&CK matrix is so comprehensive that every technique includes a detailed description of the method, as well as any systems or platforms that may pertain to it. Furthermore, the MITRE ATT&CK matrix tells which adversary groups (such as cyber criminal organizations or known hackers) use a specific tactic. This can help cyber security personnel identify an attacker and formulate a better defense on the fly.
Three Iterations of the MITRE ATT&CK Framework
In the MITRE ATT&CK framework’s modern version, there are three iterations or versions of the matrix that organizations can use depending on what best suits their needs. These iterations are:
· MITRE ATT&CK for Enterprise. This matrix emphasizes adversarial behavior in traditional and enterprise-level Windows, Mac, Linux, and cloud environments
· MITRE ATT&CK for Mobile. This matrix emphasizes adversarial behavior in mobile operating systems for iOS and Android devices
· MITRE ATT&CK for ICS. This matrix emphasizes adversarial behavior if operating within an ICS network
Thanks to these matrixes, cyber security teams can choose the matrix that suits their organization. For example, an enterprise-level business might use the MITRE ATT&CK for Enterprise matrix to help defend against enterprise-level attacks, like data breaches. Meanwhile, a mobile developer’s cyber security team might better benefit from the MITRE ATT&CK for Mobile matrix.
History of the MITRE ATT&CK Framework
MITRE is a nonprofit cyber security organization that offers engineering and technical advice to the federal government. The MITRE ATT&CK framework was originally developed for a research project in 2013, with the goal of collecting data on common cyber security attacks.
However, the MITRE ATT&CK framework was released in 2015 to the public for free. That allows organizations of all sizes to take advantage of it to help their security teams better protect their data against cyber attacks.
The goal of the MITRE ATT&CK framework was to improve “post-compromise” digital threat detection. In essence, the researchers wanted to help cyber security teams achieve better results against modern digital threats like malware attacks and phishing attacks.
Originally, the MITRE ATT&CK framework focused on threats only against Windows enterprise systems. Nowadays, the framework includes defenses and comprehensive advice for Linux, macOS, ICS, and mobile operating systems as well.
The cyber kill chain, developed by Lockheed Martin, is similar to the MITRE ATT&CK framework. However, the MITRE ATT&CK framework is better in many cases since it identifies specific techniques used by threat actors based on real-world observations.
How Do You Use the MITRE ATT&CK Matrix/Framework?
The MITRE ATT&CK framework is so in-depth and comprehensive that it is widely used as a legitimate authority to understand the techniques and behaviors that hackers use against all organizations. In short, it’s a valuable educational tool for cyber security personnel since it removes ambiguity and breaks down common tactics step-by-step.
However, you can also use the MITRE ATT&CK framework and matrix for specific use cases. Here are some example use cases for the MITRE ATT&CK.
Prioritize Detections
Even if your cyber security team has a lot of resources, you can’t protect against all potential digital vectors equally. By using the MITRE ATT&CK framework, your teams can focus their cyber threat detection efforts more directly.
For instance, if you know that most of your threats come from phishing emails thanks to the MITRE ATT&CK matrix, you can prioritize cyber security efforts in that arena. Alternatively, you can use the MITRE ATT&CK matrix to prioritize specific, relevant detections based on the techniques used by hacker or attacker groups that are prevalent in your industry.
In short, by prioritizing detections, the MITRE ATT&CK framework allows your cyber security team to make the most of its limited resources at all times.
Evaluate Defenses
Additionally, the MITRE ATT&CK framework allows you to evaluate your current defenses and figure out ways to improve your cyber security. In some areas, for instance, your team might feel confident in its depth of detection, while feel less confident in others.
You can use the MITRE ATT&CK framework to define common or priority threats for your organization. Then your team can look at your current defenses against those threats and make improvements if necessary. This is especially useful for red-teaming activities since the matrix can help you define the scope of a red-teaming exercise and be used as a scorecard during or after the test.
Track Attacker Groups
You can use the MITRE ATT&CK framework to track different attacker groups. For instance, if you want to prioritize tracking a specific adversary or criminal group that is known to be a threat to your industry, you can use the MITRE ATT&CK framework to do just that.
That’s doubly true since the MITRE ATT&CK framework is not static. MITRE is always evolving the framework as new threats emerge and become more prevalent. Because of this, you can recheck the MITRE ATT&CK from time to time to understand how different hacker groups and techniques change and adapt to your cyber security.
What is MITRE ATT&CK Mapping?
MITRE ATT&CK mapping is the science of tracking different hacker techniques and tactics across the globe. In this way, organizations can understand which hacker groups are most likely to be threats to their operations. Then they can use that information to better direct their security efforts.
Cyber security teams can map different MITRE ATT&CK tactics and techniques to see how the global cyber security situation evolves. This visualization can be especially helpful for understanding broad, global trends.
Where Does MITRE ATT&CK Framework Data Come From?
The MITRE ATT&CK framework uses publicly available threat intelligence and incident reporting data. In other words, organizations and cyber security firms of all types supply the crucial data that MITRE uses to keep its matrix up-to-date and relevant for all industries.
Furthermore, the MITRE ATT&CK framework takes much of its data from new research techniques that are contributed by threat hunters and cyber security analysts. Many of those professionals then use the MITRE ATT&CK framework to understand how bad actors or hackers might act.
In this way, the MITRE ATT&CK framework has a symbiotic relationship with the cyber security community as a whole.
Wrap Up
The MITRE ATT&CK framework is an in-depth and useful knowledge base and cyber adversary behavior model, helping cyber security teams and experts better understand cyber criminals and anticipate potential attacks. Through the smart use of MITRE ATT&CK tactics and techniques, security personnel can perform offensive and defensive cyber security actions for greater results.
It’s an important part of using PC Matic’s security software solutions, as well. PC Matic Pro and MSP both benefit from the MITRE ATT&CK framework’s information and approaches. Contact us today to learn how our security solution can help your business enjoy maximum cyber security for years to come.




