A Day Like Any Other
It was a typical morning for Travis. He had just logged into a major upgrade meeting with his team when he received a phone call. The call came from an 800 number. Used to receiving numerous calls from various sources, Travis quickly Googled the number, which appeared to be from Wells Fargo Bank. Trusting the source, he answered.
The Deceptive Call
The caller introduced himself as a representative from the Wells Fargo Fraud Department, informing Travis of a suspicious transaction in Maryland. This scenario wasn’t new to Travis; he had received similar legitimate calls. The caller’s American accent and calm demeanor further disarmed Travis. The request to verify his identity by reading back a code sent via text seemed routine.
The Red Flags Overlooked
Travis didn’t scrutinize the text messages closely, distracted by his work meeting. He received a code, which he promptly read back to the caller. The scammer then suggested changing his PIN, a plausible request given the context of fraud prevention. Travis was transferred to what sounded like an automated system to change his PIN, a process he had undergone before.
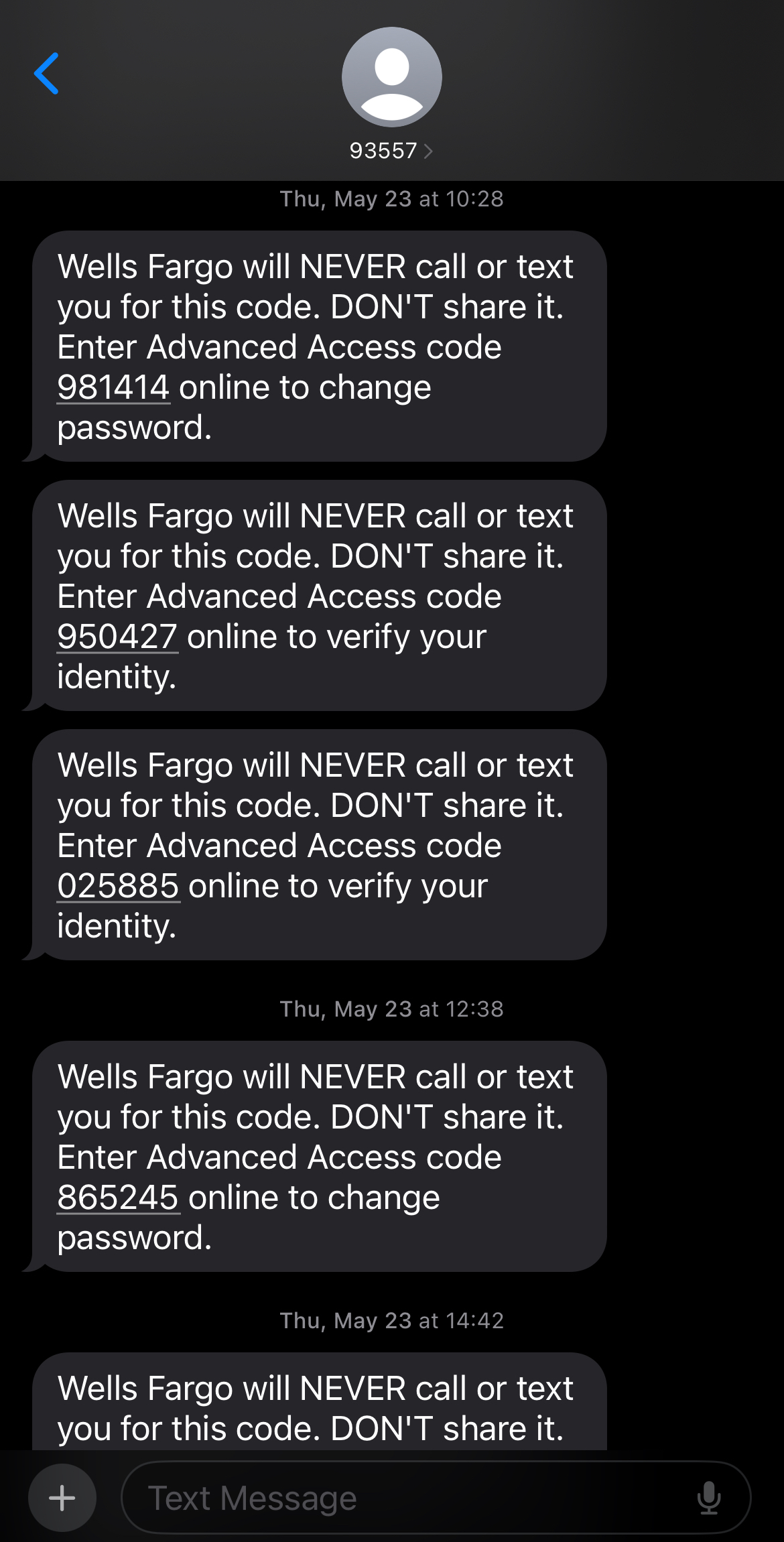
The Unfolding Scam
During the call, Travis began receiving emails from Wells Fargo about changes to his account, including a password change and a significant $2,400 credit card transfer. Maintaining his calm and reassuring demeanor, the scammer dismissed these as delayed system notifications. Still multitasking between his work meeting and the call, Travis didn’t give these alerts the attention they warranted.
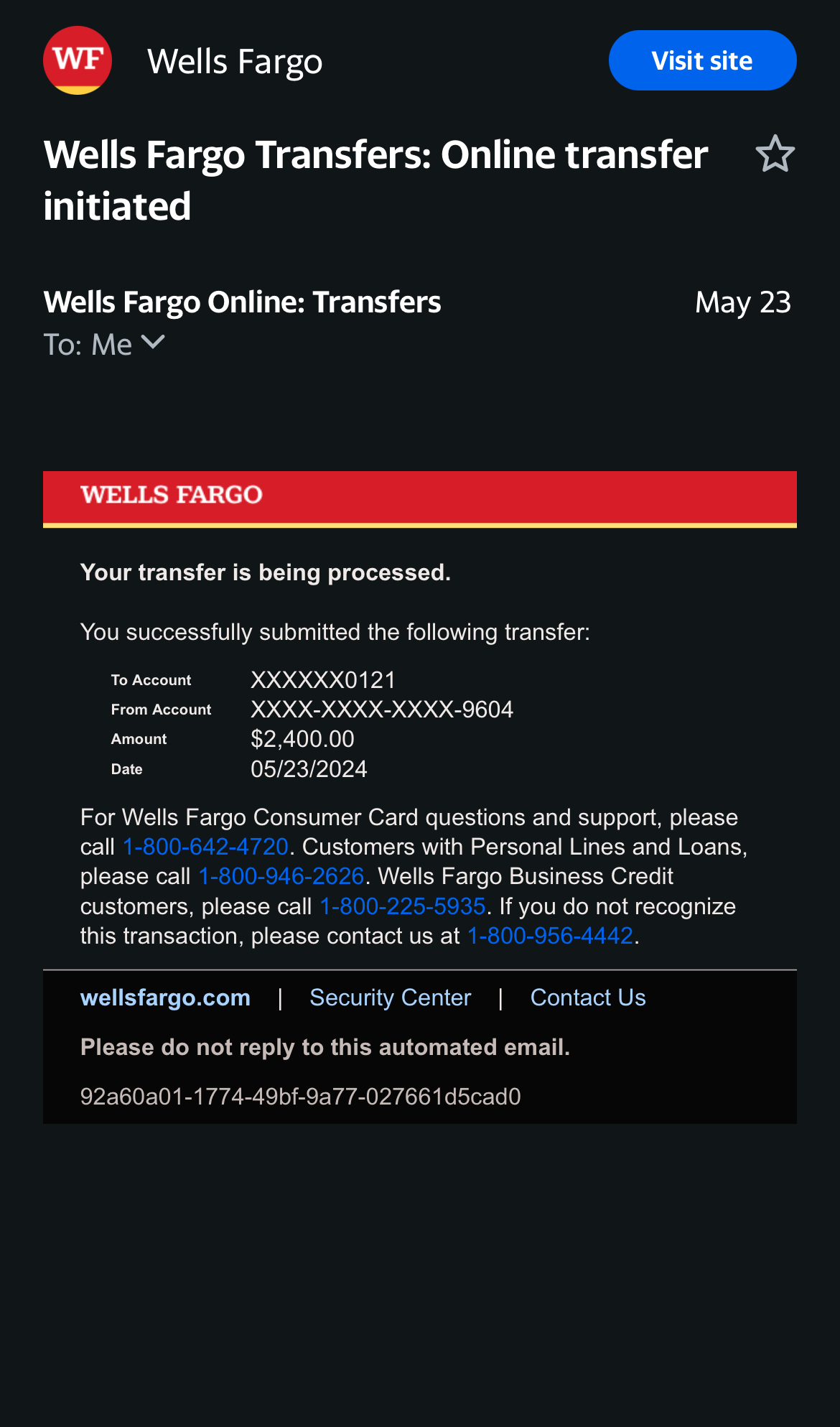
Realization and Damage Control
After over an hour on the call, including multiple holds filled with typical bad-hold music, Travis started to feel uneasy. The prolonged duration and continuous requests for verification codes raised his suspicion. Finally, he hung up on the scammer and called Wells Fargo’s customer service directly.
The Aftermath
Upon reaching the real Wells Fargo representatives, Travis learned that his account had been compromised. The scammers changed his password, transferred funds, and even enrolled his account in Samsung Pay. Despite the eventual resolution and securing of his account, the incident was a sobering experience for Travis.
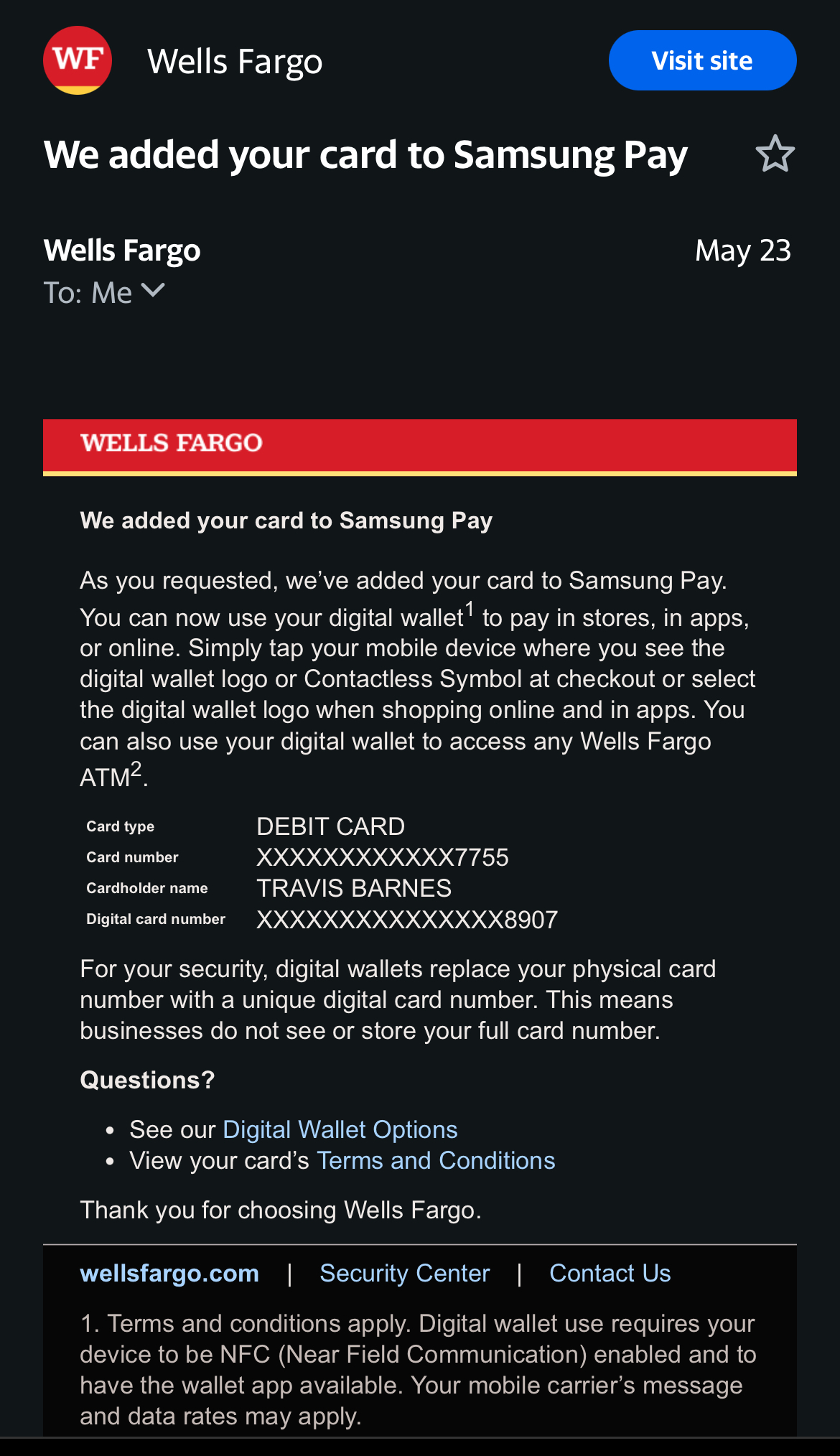
Lessons Learned
Travis’ experience underscores the importance of vigilance, even when dealing with seemingly legitimate scenarios. Here are some key takeaways to protect yourself from similar scams:
1. Verify Sources Independently:
If you receive a suspicious call, hang up and contact your bank directly using the phone number on their official website.
2. Scrutinize All Communications:
Pay close attention to messages and emails, especially those involving access codes or account activity.
3. Limit Multitasking During Important Calls:
Avoid handling sensitive tasks when you’re distracted by other activities.
4. Report Fraud and Document:
Immediately report any suspicious activity to your bank and document the incident for future reference.
Email any suspicious email, text message, or phone call to [email protected].
Understanding the Scam
This scam is a classic example of phishing, where imposters use fake and fraudulent accounts to deceive victims into providing sensitive information. The scammer had all the trappings of a legitimate bank representative, leveraging common tactics such as spoofing contact information and using malware to intercept authentication codes. The goal was identity theft, gaining access to Travis’ online banking details, and manipulating his Wells Fargo account.
Travis hopes to raise awareness and help others avoid becoming victims of such sophisticated scams. Stay alert, and always verify before you trust. Remember, even a trusted financial institution like Wells Fargo can be used by fraudsters to create a facade of legitimacy.